Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 13 julho 2024

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

101 Landing Page Optimization Tips & Ideas

NET Program Execution Process - Dot Net Tutorials

How to Fix a Toxic Culture

PHP 8.2: New Features, Deprecations, and Bug Fixes
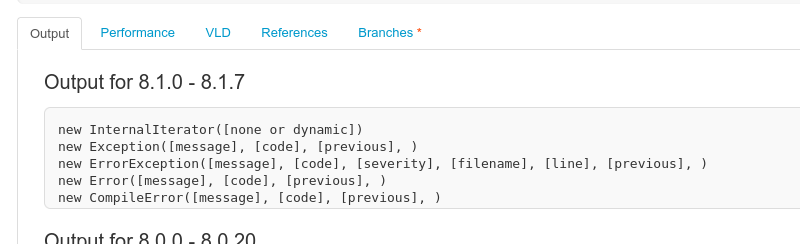
PHP - RCE abusing object creation: new $_GET[a]($_GET[b

6379 - Pentesting Redis - HackTricks

The Lancet Commission on the future of care and clinical research

Hunting for Suspicious Windows Libraries for Execution and Defense

Nested Exceptions in Java: Definition & Example - Video & Lesson
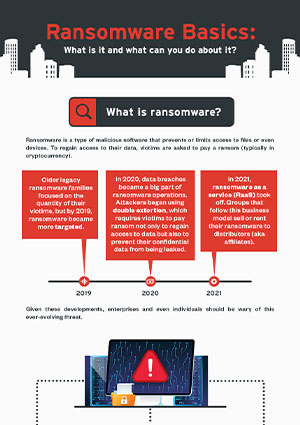
Ransomware - Definition

HIPAA Compliance Checklist 2024

General Tools Digital Angle Finder Ruler #822 - 5 Stainless Steel

Orange: Hacking Jenkins Part 2 - Abusing Meta Programming for
Aligning Substance Abuse Confidentiality Regulations With HIPAA to

TryHackMe OWASP Top 10 - 2021
Recomendado para você
-
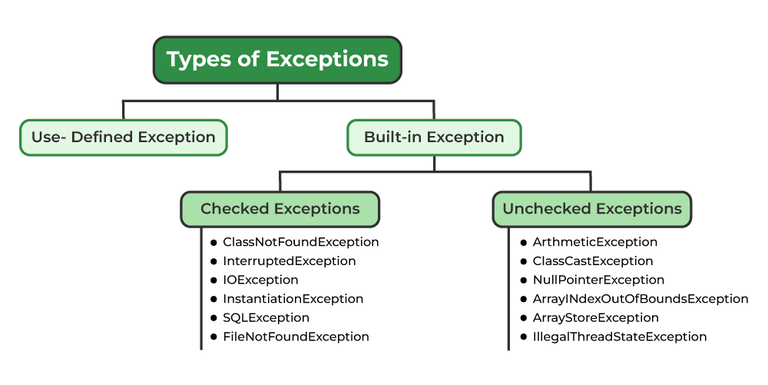 Exception Handling in Java: Types, Custom Exceptions, and Hierarchy Rules13 julho 2024
Exception Handling in Java: Types, Custom Exceptions, and Hierarchy Rules13 julho 2024 -
 Exception & Error Handling in Python, Tutorial by DataCamp13 julho 2024
Exception & Error Handling in Python, Tutorial by DataCamp13 julho 2024 -
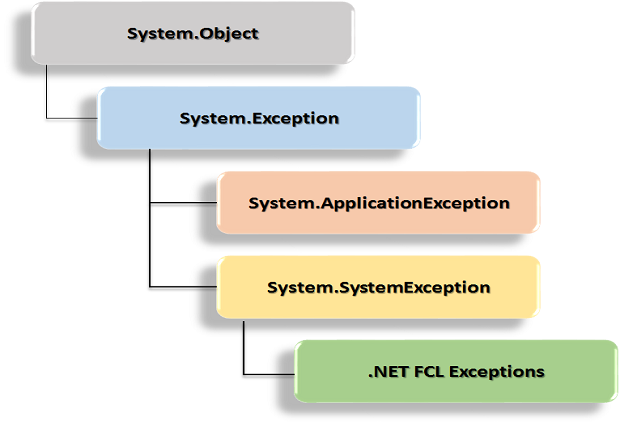 Best practices in handling exceptions in C#13 julho 2024
Best practices in handling exceptions in C#13 julho 2024 -
 Dress Expectations / Dress Code Exceptions13 julho 2024
Dress Expectations / Dress Code Exceptions13 julho 2024 -
 Auditing Exceptions and How They Might Impact Your SOC Reports13 julho 2024
Auditing Exceptions and How They Might Impact Your SOC Reports13 julho 2024 -
 Selenium WebDriver: Handling Exceptions, Blog13 julho 2024
Selenium WebDriver: Handling Exceptions, Blog13 julho 2024 -
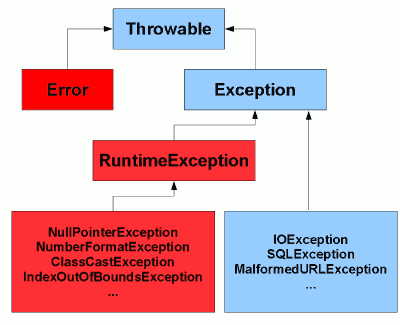 The exception hierarchy in Java13 julho 2024
The exception hierarchy in Java13 julho 2024 -
 What is the built in base class to handle all exceptions in Java - Stack Overflow13 julho 2024
What is the built in base class to handle all exceptions in Java - Stack Overflow13 julho 2024 -
Handle Exceptions - OutSystems 11 Documentation13 julho 2024
-
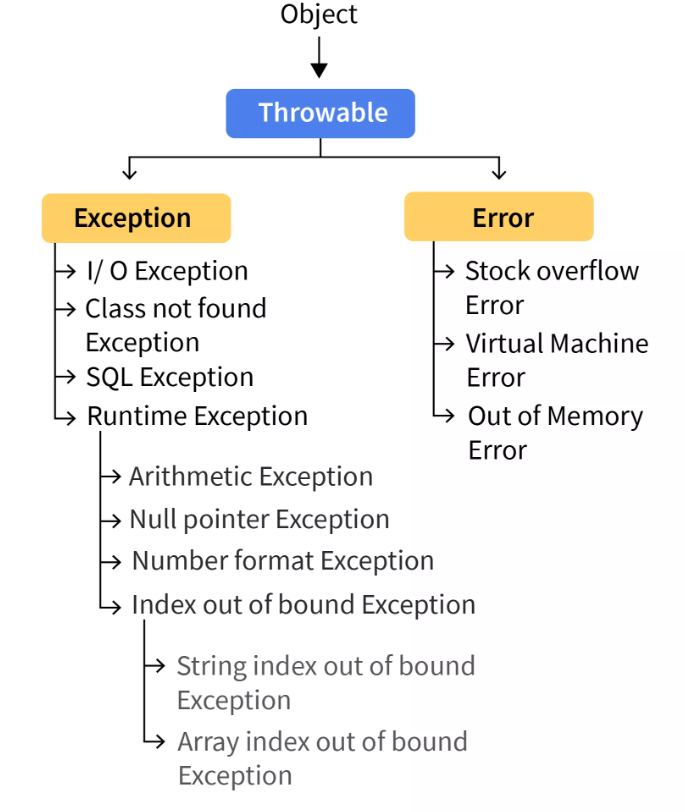 Exception Handling in Java. Exception Handling in Java is one of…, by Abhijeet Verma13 julho 2024
Exception Handling in Java. Exception Handling in Java is one of…, by Abhijeet Verma13 julho 2024
você pode gostar
-
 Top 10 Casual 2 Player Games - Not Just For Couples!!13 julho 2024
Top 10 Casual 2 Player Games - Not Just For Couples!!13 julho 2024 -
 Download GAMEE Prizes: Real Money Games APK for Android, Play on PC and Mac13 julho 2024
Download GAMEE Prizes: Real Money Games APK for Android, Play on PC and Mac13 julho 2024 -
Tuesdays With Morrie, South San Francisco Public Library13 julho 2024
-
Retro Dodo on X: Here's our Top 15 PSP Games Of All Time. 😍 Is13 julho 2024
-
Netflix's 'Dog and Boy' anime causes outrage for incorporating AI13 julho 2024
-
 File:Mestre Casagrande.jpg - Wikimedia Commons13 julho 2024
File:Mestre Casagrande.jpg - Wikimedia Commons13 julho 2024 -
 Is There a Sonic Prime Episode 9 Coming Out on Netflix? - GameRevolution13 julho 2024
Is There a Sonic Prime Episode 9 Coming Out on Netflix? - GameRevolution13 julho 2024 -
 ArtStation - Éowyn, Lady of Rohan13 julho 2024
ArtStation - Éowyn, Lady of Rohan13 julho 2024 -
/i.s3.glbimg.com/v1/AUTH_bc8228b6673f488aa253bbcb03c80ec5/internal_photos/bs/2018/A/C/x8q39BSgyIPLNGyl0Ipg/2018-06-15t180505z-209886665-rc1982b4b3e0-rtrmadp-3-soccer-worldcup-por-esp.jpg) Portugal 3 x 3 Espanha Copa do Mundo da FIFA™: melhores momentos13 julho 2024
Portugal 3 x 3 Espanha Copa do Mundo da FIFA™: melhores momentos13 julho 2024 -
 /media/cache/1d/e4/1de4baee30f3a213 julho 2024
/media/cache/1d/e4/1de4baee30f3a213 julho 2024
