Malware analysis Malicious activity
Por um escritor misterioso
Last updated 08 julho 2024

Malware Analysis: Steps & Examples - CrowdStrike

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

Malware analysis method Download Scientific Diagram

Interactive Online Malware Sandbox

StopRansomware: Rhysida Ransomware
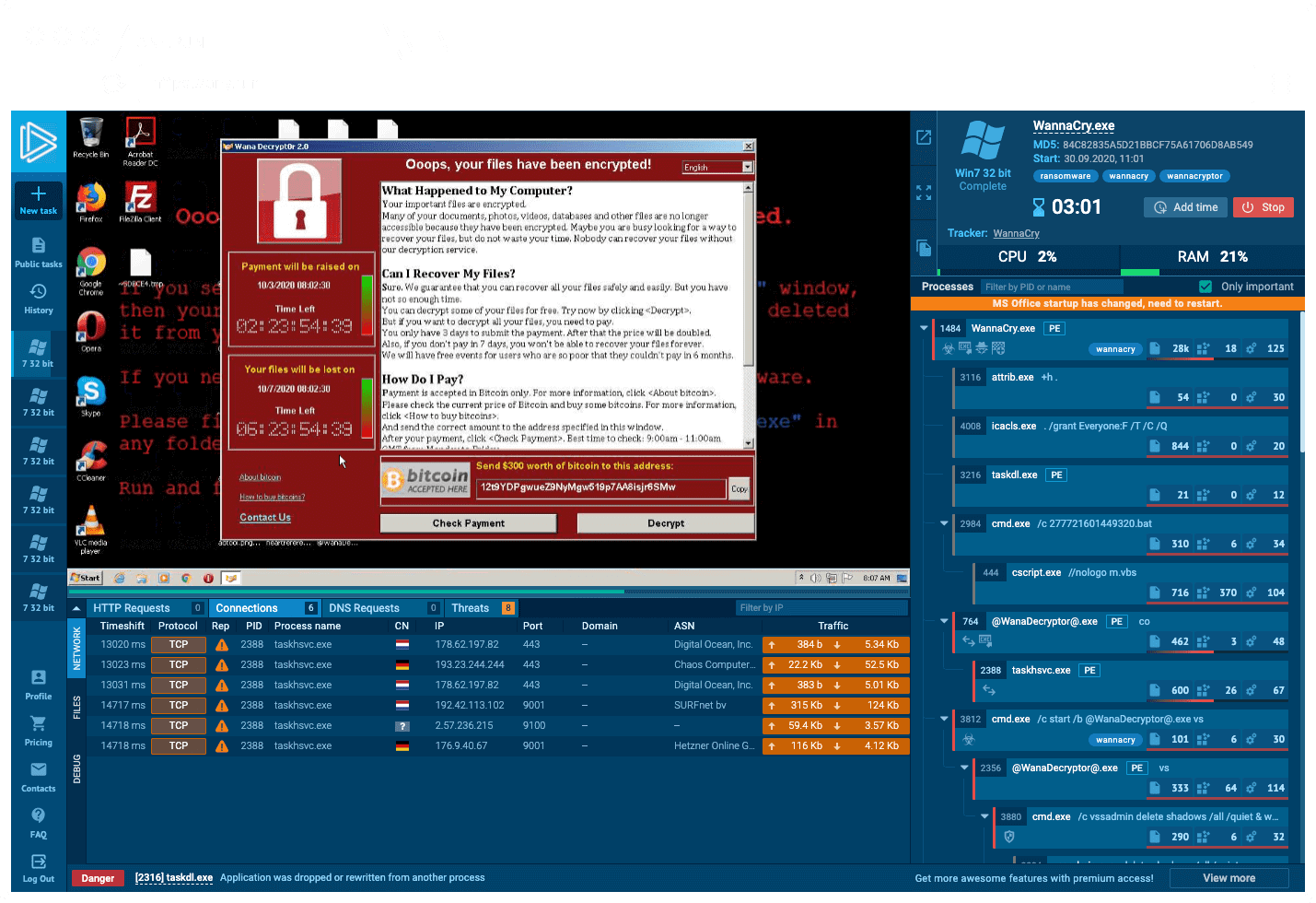
Interactive Online Malware Sandbox

Security Orchestration Use Case: Automating Malware Analysis
Malware analysis what.exe Malicious activity

PROUD-MAL: static analysis-based progressive framework for deep

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Mastering Malware Analysis

Routers Roasting on an Open Firewall: the KV-botnet Investigation

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
www.roblox.com - see bug description · Issue #45398 · webcompat/web-bugs · GitHub08 julho 2024
-
![How to Update Roblox The Right Way [PC & Mac] - Alvaro Trigo's Blog](https://alvarotrigo.com/blog/assets/imgs/2022-09-11/choose-game.jpeg) How to Update Roblox The Right Way [PC & Mac] - Alvaro Trigo's Blog08 julho 2024
How to Update Roblox The Right Way [PC & Mac] - Alvaro Trigo's Blog08 julho 2024 -
Avatar Editor - Roblox08 julho 2024
-
 Top Free Roblox Templates Users Should Know About - BrightChamps Blog08 julho 2024
Top Free Roblox Templates Users Should Know About - BrightChamps Blog08 julho 2024 -
Discover - Roblox08 julho 2024
-
 How to Sign Up for an Account on Roblox: 6 Steps (with Pictures)08 julho 2024
How to Sign Up for an Account on Roblox: 6 Steps (with Pictures)08 julho 2024 -
 How to Choose a Roblox Username: 7 Steps (with Pictures) - wikiHow08 julho 2024
How to Choose a Roblox Username: 7 Steps (with Pictures) - wikiHow08 julho 2024 -
 Login - Roblox Roblox, Login, Social platform08 julho 2024
Login - Roblox Roblox, Login, Social platform08 julho 2024 -
 New posts in general 😐 - ROBLOX Community on Game Jolt08 julho 2024
New posts in general 😐 - ROBLOX Community on Game Jolt08 julho 2024 -
 How to log in to your roblox website account08 julho 2024
How to log in to your roblox website account08 julho 2024
você pode gostar
-
 Andrea Botez, Wiki Dream Team08 julho 2024
Andrea Botez, Wiki Dream Team08 julho 2024 -
Cress/PA - 1ª Região08 julho 2024
-
 Wiki Guilty Crown08 julho 2024
Wiki Guilty Crown08 julho 2024 -
 Retro Gran Turismo sep 2016 Hot wheels cars toys, Hot wheels, Hot wheels cars08 julho 2024
Retro Gran Turismo sep 2016 Hot wheels cars toys, Hot wheels, Hot wheels cars08 julho 2024 -
 Cyberpunk Wallpaper 4K, Futuristic, Neon background08 julho 2024
Cyberpunk Wallpaper 4K, Futuristic, Neon background08 julho 2024 -
 MAPS FOR FANTASY RPGs 4 & 5 - ROYALTY FREE MAPS by Laidback Dungeon Master — Kickstarter08 julho 2024
MAPS FOR FANTASY RPGs 4 & 5 - ROYALTY FREE MAPS by Laidback Dungeon Master — Kickstarter08 julho 2024 -
Buy Plants vs. Zombies Garden Warfare08 julho 2024
-
 O estilo de vida Hare Krishna e a contemporaneidade, by Uma Questão de Fé, Uma questão de fé08 julho 2024
O estilo de vida Hare Krishna e a contemporaneidade, by Uma Questão de Fé, Uma questão de fé08 julho 2024 -
 Category:Pokédex, Pokémon Wiki08 julho 2024
Category:Pokédex, Pokémon Wiki08 julho 2024 -
 Glitch text generator (ℂ𝕠𝕡𝕪 𝕒𝕟𝕕 ℙ𝕒𝕤𝕥𝕖)08 julho 2024
Glitch text generator (ℂ𝕠𝕡𝕪 𝕒𝕟𝕕 ℙ𝕒𝕤𝕥𝕖)08 julho 2024