Malware analysis Malicious activity
Por um escritor misterioso
Last updated 10 julho 2024

Malware Analysis: Steps & Examples - CrowdStrike

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
Malware analysis Malicious activity

How to Analyze Malware's Network Traffic in A Sandbox

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Routers Roasting on an Open Firewall: the KV-botnet Investigation - Lumen

How to Analyze Malware's Network Traffic in A Sandbox

Malware Analysis Benefits Incident Response
Lab 6-1 Solutions - Practical Malware Analysis [Book]

Endpoint Detection and Response, Free - What is EDR Security?
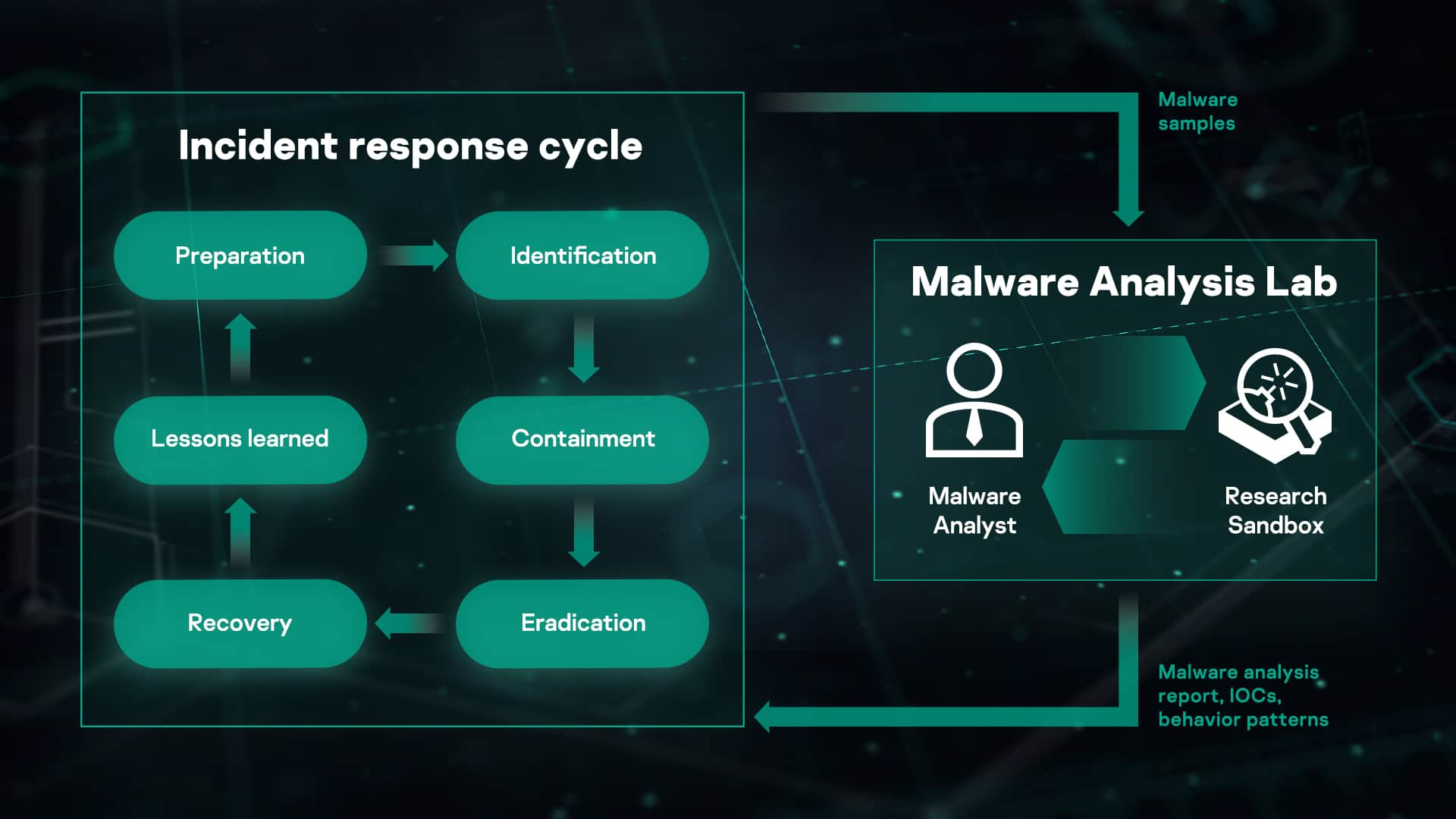
Advanced Automated Malware Analysis – Kaspersky Research Sandbox
Recomendado para você
-
 Jjsploit V4-Www.Wearedevs.Net - Colaboratory10 julho 2024
Jjsploit V4-Www.Wearedevs.Net - Colaboratory10 julho 2024 -
 EXPLOITS - BLOXEXPLOITS10 julho 2024
EXPLOITS - BLOXEXPLOITS10 julho 2024 -
 Wearedevs10 julho 2024
Wearedevs10 julho 2024 -
2023 Delta exploits for #videos10 julho 2024
-
 Roblox Aimbot Script with JJSploit Lua Executor10 julho 2024
Roblox Aimbot Script with JJSploit Lua Executor10 julho 2024 -
Infinite Jump10 julho 2024
-
 Why cant i use krnl : r/Krnl10 julho 2024
Why cant i use krnl : r/Krnl10 julho 2024 -
 Malware analysis Malicious activity10 julho 2024
Malware analysis Malicious activity10 julho 2024 -
 JJSploit can execute Dark Hub, Owlhub, Snow Hub, and more now10 julho 2024
JJSploit can execute Dark Hub, Owlhub, Snow Hub, and more now10 julho 2024 -
 Malware analysis Malicious10 julho 2024
Malware analysis Malicious10 julho 2024
você pode gostar
-
![metacritic on X: Forza Motorsport 2005 [Xbox - 92]](https://pbs.twimg.com/media/F7j2UH-asAAstIG.png) metacritic on X: Forza Motorsport 2005 [Xbox - 92]10 julho 2024
metacritic on X: Forza Motorsport 2005 [Xbox - 92]10 julho 2024 -
 gifs, cartoon and cool - image #6269272 on10 julho 2024
gifs, cartoon and cool - image #6269272 on10 julho 2024 -
 The Game of Life: Twists and Turns Replacement Pieces: 84 Life Cards FULL DECK10 julho 2024
The Game of Life: Twists and Turns Replacement Pieces: 84 Life Cards FULL DECK10 julho 2024 -
 8 in 1 Games - Electronic Chess with Exercise & Talking Tutor Function – Croove10 julho 2024
8 in 1 Games - Electronic Chess with Exercise & Talking Tutor Function – Croove10 julho 2024 -
 Guren Ichinose MBTI Personality Type: ENTJ or ENTP?10 julho 2024
Guren Ichinose MBTI Personality Type: ENTJ or ENTP?10 julho 2024 -
 I hate fillers : r/zatchbell10 julho 2024
I hate fillers : r/zatchbell10 julho 2024 -
 WarGroove: o Sapateado Medieval perante a Música de Guerra – Rubber Chicken10 julho 2024
WarGroove: o Sapateado Medieval perante a Música de Guerra – Rubber Chicken10 julho 2024 -
Cowboy yoga music? 'Red Dead Redemption 2' composer Woody Jackson conjures Western spirits - Los Angeles Times10 julho 2024
-
 Prefeitura de São Paulo - Sala de imprensa10 julho 2024
Prefeitura de São Paulo - Sala de imprensa10 julho 2024 -
 The Queen's Gambit 👑♟️👩🏻🦰 on X: Moses Ingram makes her next move. #ObiWan #TheQueensGambit #MosesIngram / X10 julho 2024
The Queen's Gambit 👑♟️👩🏻🦰 on X: Moses Ingram makes her next move. #ObiWan #TheQueensGambit #MosesIngram / X10 julho 2024

