Malware analysis Malicious activity
Por um escritor misterioso
Last updated 29 julho 2024

FBI, CISA, MS-ISAC release cybersecurity advisory on emerging Rhysida ransomware targeting critical sectors - Industrial Cyber

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Dynamic malware analysis [34]
TryHackMe Hacktivities

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

What is Malware? Definition, Types, Prevention - TechTarget
Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware: 9781788392501: A,

Learning Malware Analysis: Explore the concepts, tools, and techniques to analyze and investigate Windows malware

Patch Now: Exploit Activity Mounts for Dangerous Apache Struts 2 Bug

MetaDefender Cloud Advanced threat prevention and detection
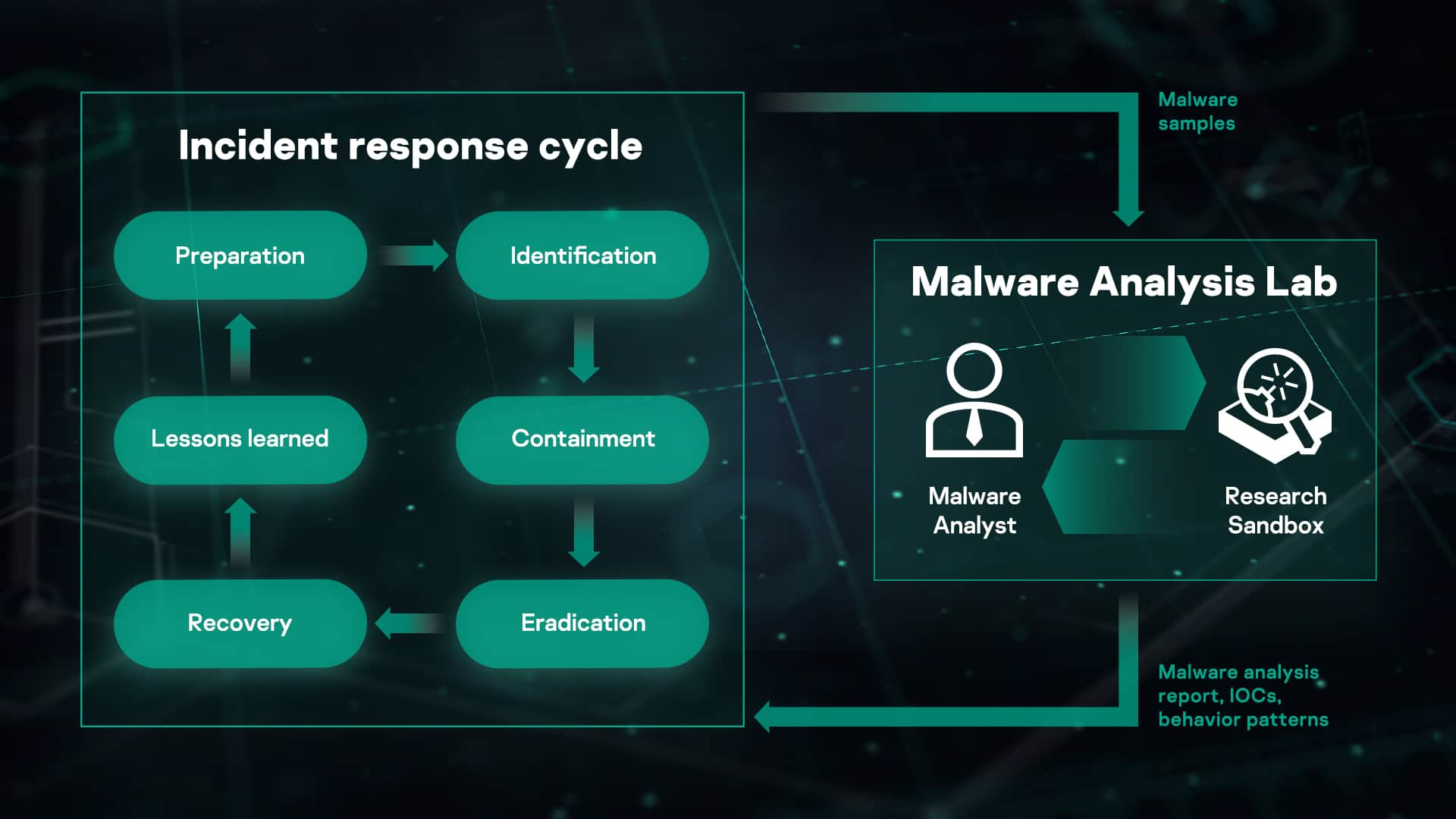
Advanced Automated Malware Analysis – Kaspersky Research Sandbox

Malware analysis file Malicious activity

What Is Malware Analysis? Definition, Types, Stages, and Best Practices - Spiceworks
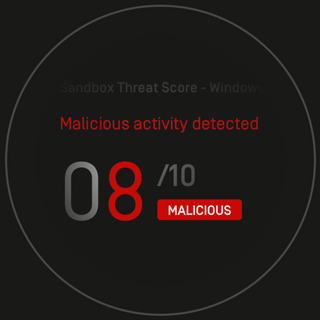
MetaDefender Cloud Advanced threat prevention and detection

How to Do Malware Analysis?

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs
Recomendado para você
-
2,000 Most Common Arabic Words29 julho 2024
-
 Coffee Pdf Cafe Du Jour Pdf Cafe Pdf Coffee Shop Pdf Cafe29 julho 2024
Coffee Pdf Cafe Du Jour Pdf Cafe Pdf Coffee Shop Pdf Cafe29 julho 2024 -
 Pdfcoffee - How will sign and return to the ebook unavailable right now - Download Complete File - Studocu29 julho 2024
Pdfcoffee - How will sign and return to the ebook unavailable right now - Download Complete File - Studocu29 julho 2024 -
 ANTARES.pdf29 julho 2024
ANTARES.pdf29 julho 2024 -
 pdfcoffee.com_skyfall-adele-pdf-free Pages 1-7 - Flip PDF Download29 julho 2024
pdfcoffee.com_skyfall-adele-pdf-free Pages 1-7 - Flip PDF Download29 julho 2024 -
 SOLUTION: Pdfcoffee com advanced mechanics of materials and applied elasticity 5th edition solutions manual pdf free - Studypool29 julho 2024
SOLUTION: Pdfcoffee com advanced mechanics of materials and applied elasticity 5th edition solutions manual pdf free - Studypool29 julho 2024 -
Science Visual Resources Physics : The Diagram Group, Derek Mc Monagle : Free Download, Borrow, and Streaming : Internet Archive29 julho 2024
-
 SOLUTION: Pdfcoffee com dark psychology 3 books in 1 manipulation and dark psychology persuasion and dark psychology dark nlp the definitive guide to detect and defend yourself from dark psychology secrets pdf29 julho 2024
SOLUTION: Pdfcoffee com dark psychology 3 books in 1 manipulation and dark psychology persuasion and dark psychology dark nlp the definitive guide to detect and defend yourself from dark psychology secrets pdf29 julho 2024 -
 Modern Jazz Guitar Chord Concepts - Fundamental Changes Music Book Publishing29 julho 2024
Modern Jazz Guitar Chord Concepts - Fundamental Changes Music Book Publishing29 julho 2024 -
 Coffee cross stitch pattern PDF, Coffee cup modern cute easy cross stitch pattern for beginners. Cross stitch tea cups .: generic: : Books29 julho 2024
Coffee cross stitch pattern PDF, Coffee cup modern cute easy cross stitch pattern for beginners. Cross stitch tea cups .: generic: : Books29 julho 2024
você pode gostar
-
 089/193 Spiritomb Paldea Evolved (SV02)29 julho 2024
089/193 Spiritomb Paldea Evolved (SV02)29 julho 2024 -
 Bebe Reborn Danny Elo7 Produtos Especiais29 julho 2024
Bebe Reborn Danny Elo7 Produtos Especiais29 julho 2024 -
ESPN FC - Spartak Moscow are here for disillusioned fans of clubs in the European Super League.29 julho 2024
-
 Assistir Boruto: Naruto Next Generations - Episódio 54 - Meus Animes29 julho 2024
Assistir Boruto: Naruto Next Generations - Episódio 54 - Meus Animes29 julho 2024 -
 Liga Portugal 2 Qualification matches, tables and news 2022/202329 julho 2024
Liga Portugal 2 Qualification matches, tables and news 2022/202329 julho 2024 -
Five Nights at Freddy's Anime - Mangle/Toy Foxy - Wattpad29 julho 2024
-
 Gotenks super Sayajin 3, Wiki29 julho 2024
Gotenks super Sayajin 3, Wiki29 julho 2024 -
The Meme Room - Roblox29 julho 2024
-
 8bit Pixel Fruit29 julho 2024
8bit Pixel Fruit29 julho 2024 -
 Página para colorir de Kushina, Naruto e Minato - Desenhos para colorir gratuitos para imprimir29 julho 2024
Página para colorir de Kushina, Naruto e Minato - Desenhos para colorir gratuitos para imprimir29 julho 2024