Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 31 agosto 2024

Malware Incident Response Steps on Windows, and Determining If the

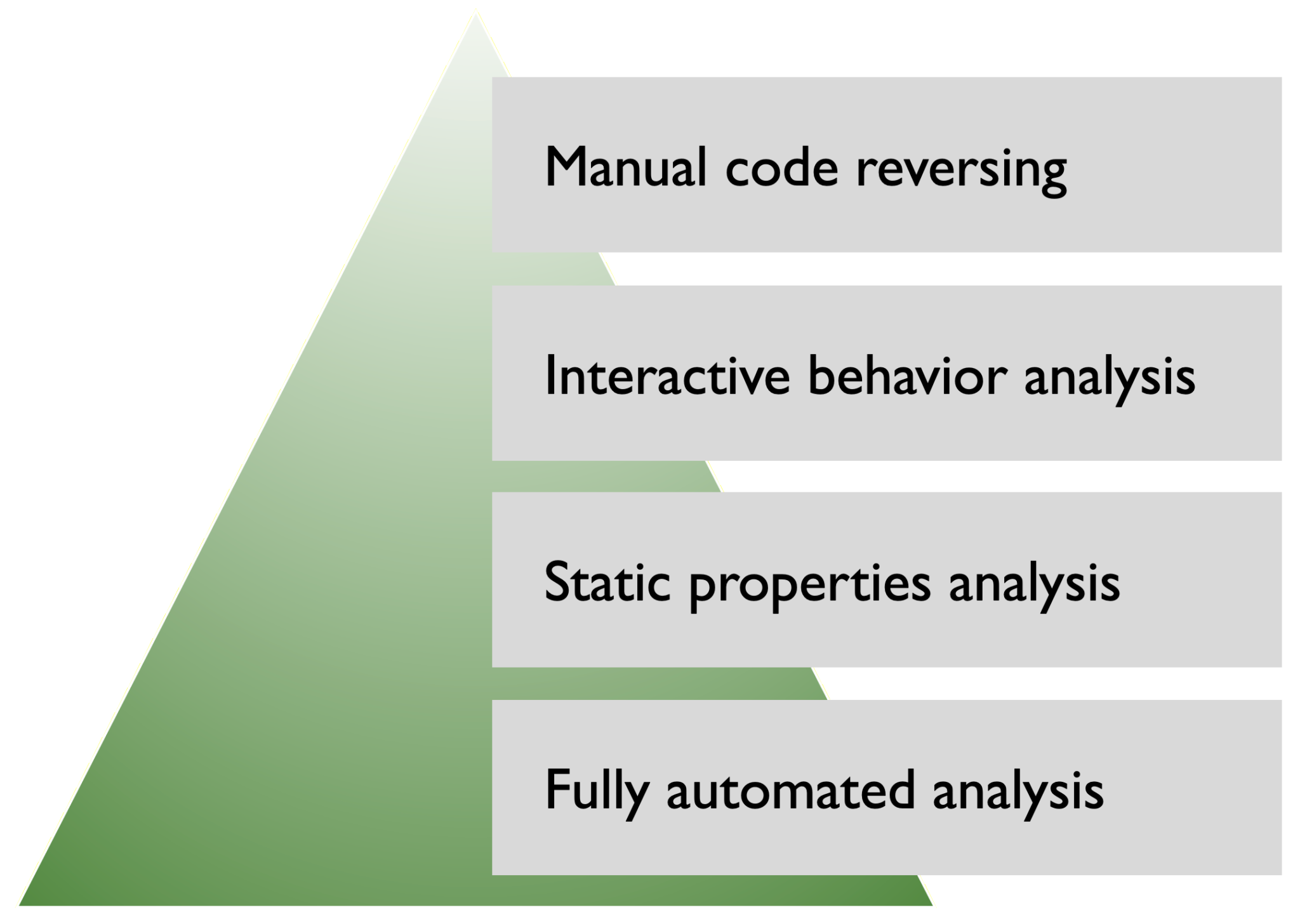
The Top 10 Malware Analysis Tools
How You Can Start Learning Malware Analysis

Microsoft 365 Alerting - Detect and React to Threats Instantly

US Cyber Command, DHS-CISA release Russian malware samples tied to

Malware Detection & Top Techniques Today
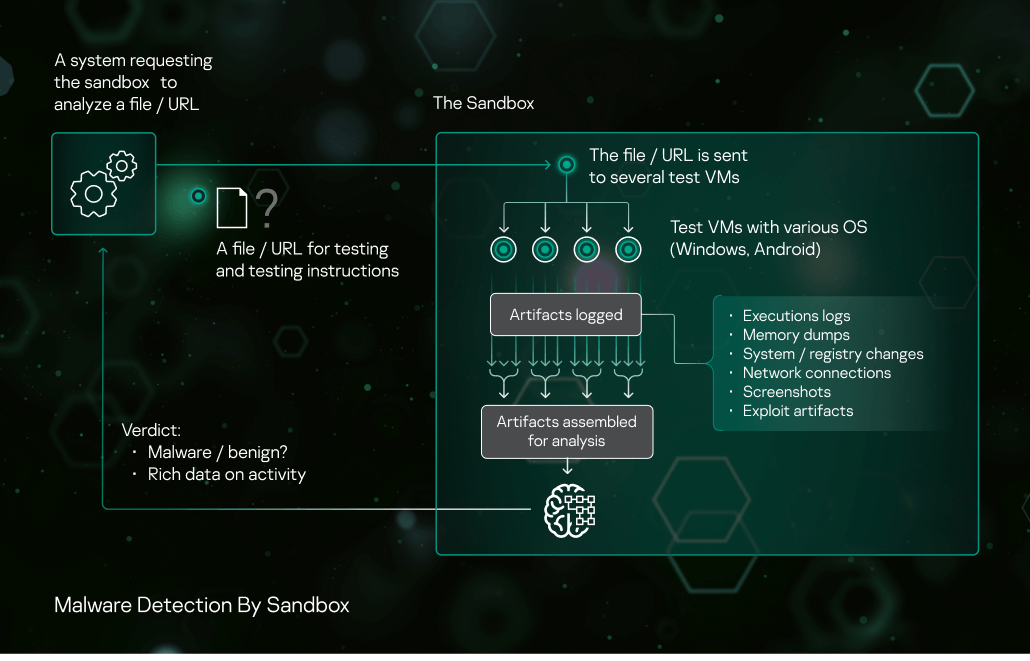
Sandbox Kaspersky
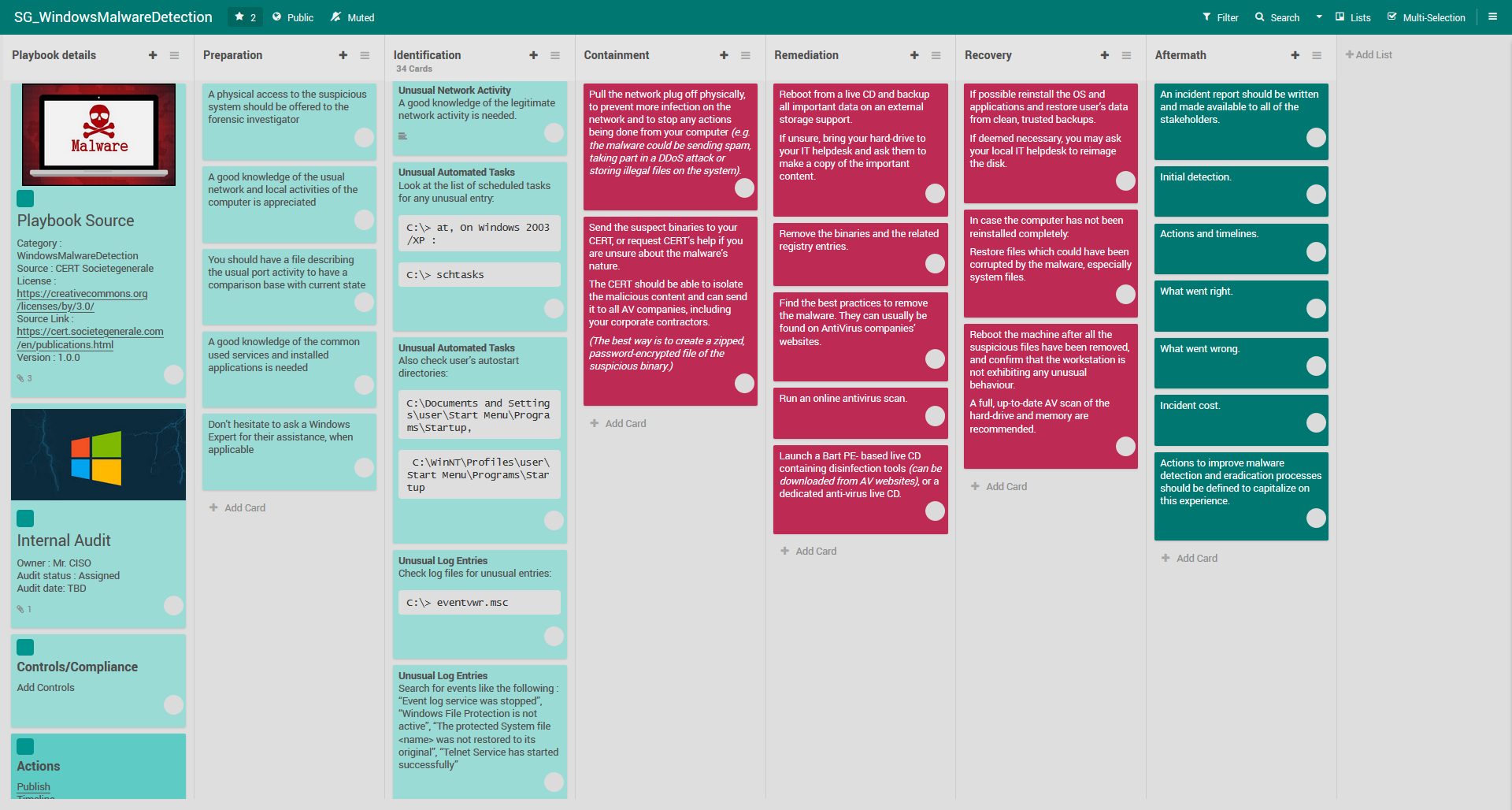
Playbook for Malware outbreak

Why Do You Need a Malware Sandbox? - Cyber Defense Magazine

What Is Malware Analysis? Definition, Types, Stages, and Best

Malware Analysis: Steps & Examples - CrowdStrike
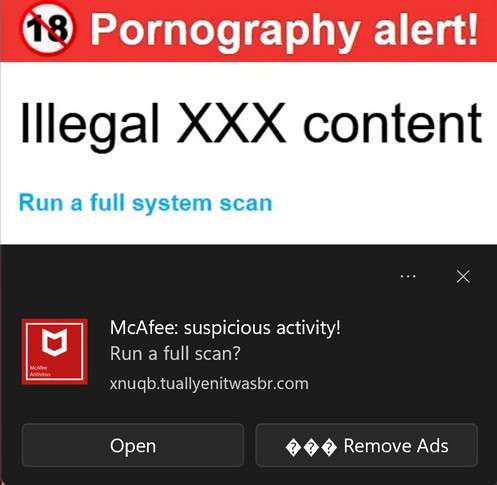
Remove McAfee Suspicious Activity Pop-ups [Virus Removal]
Recomendado para você
-
 Doing “IP Chicken” from the CLI – InfoSec Monkey31 agosto 2024
Doing “IP Chicken” from the CLI – InfoSec Monkey31 agosto 2024 -
 IPchicken at the terminal31 agosto 2024
IPchicken at the terminal31 agosto 2024 -
Ipchicken.com31 agosto 2024
-
ipchicken.com - IP Chicken - What is my IP address? Free public IP lookup. - DomainsData31 agosto 2024
-
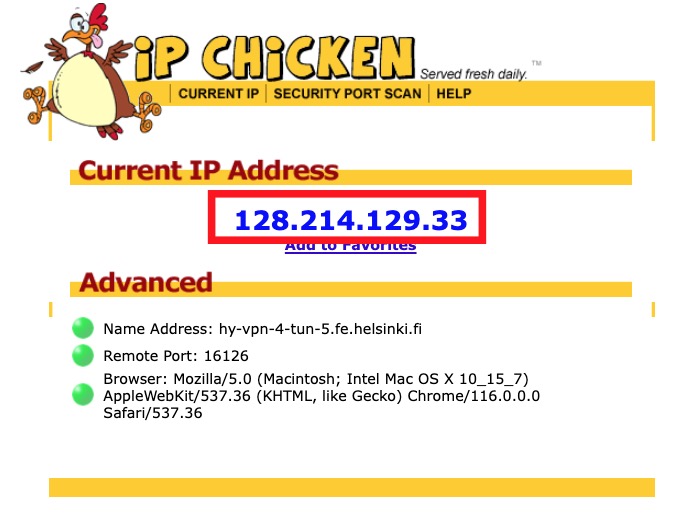 HY-VPN – Checking functionality and errors (Linux)31 agosto 2024
HY-VPN – Checking functionality and errors (Linux)31 agosto 2024 -
 Malware analysis Malicious activity31 agosto 2024
Malware analysis Malicious activity31 agosto 2024 -
 How do sites like ipchicken and whatsmyip work? : r/AskReddit31 agosto 2024
How do sites like ipchicken and whatsmyip work? : r/AskReddit31 agosto 2024 -
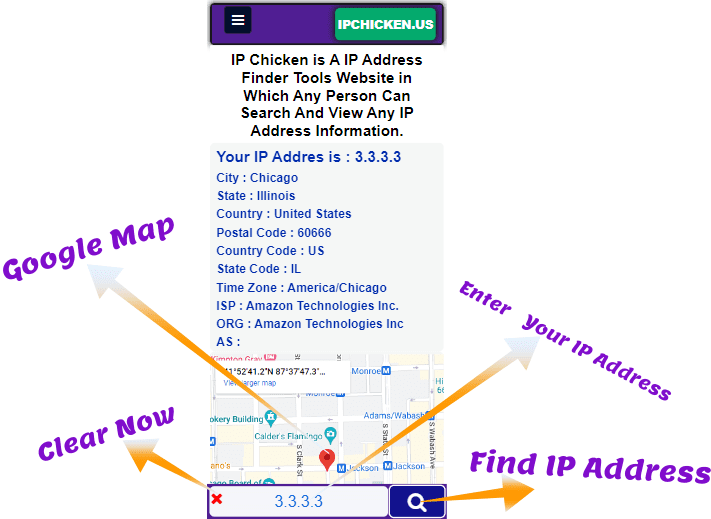 IP Chicken - What Is My IP Address See Your IP Address Free31 agosto 2024
IP Chicken - What Is My IP Address See Your IP Address Free31 agosto 2024 -
 shell - SSH socks proxy via jumphost - Stack Overflow31 agosto 2024
shell - SSH socks proxy via jumphost - Stack Overflow31 agosto 2024 -
 Tyson expands portfolio of meal shortcuts, 2021-01-2031 agosto 2024
Tyson expands portfolio of meal shortcuts, 2021-01-2031 agosto 2024
você pode gostar
-
Resident Evil' franchise takes a disturbing turn - The San Diego Union-Tribune31 agosto 2024
-
 Sonic.EXE - MISC - AK1 MUGEN Community31 agosto 2024
Sonic.EXE - MISC - AK1 MUGEN Community31 agosto 2024 -
 Nintendo Switch price isn't going up, despite higher costs: president - Nikkei Asia31 agosto 2024
Nintendo Switch price isn't going up, despite higher costs: president - Nikkei Asia31 agosto 2024 -
 What is 'Kokoro'? A meaning beyond heart or “spirit” - Kokoro Media31 agosto 2024
What is 'Kokoro'? A meaning beyond heart or “spirit” - Kokoro Media31 agosto 2024 -
 Tad thinks Jimmy is ugly : r/bully31 agosto 2024
Tad thinks Jimmy is ugly : r/bully31 agosto 2024 -
 Pappas Burger, 7800 Airport Blvd Space C14 in Houston - Restaurant menu and reviews31 agosto 2024
Pappas Burger, 7800 Airport Blvd Space C14 in Houston - Restaurant menu and reviews31 agosto 2024 -
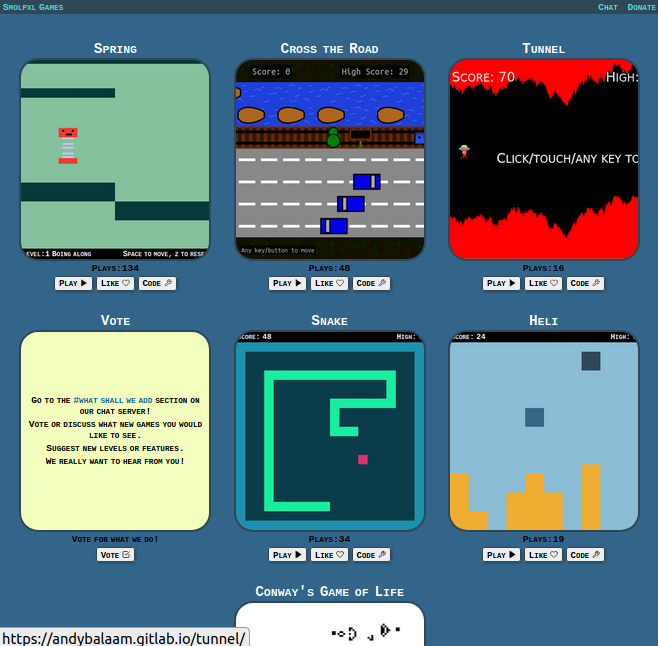 Play and create little retro games at Smolpxl – Andy Balaam's Blog31 agosto 2024
Play and create little retro games at Smolpxl – Andy Balaam's Blog31 agosto 2024 -
 Ichibansho Figure JoJo's Bizarre Adventure Jotaro Kujo (Stardust Crusaders) - Tokyo Otaku Mode (TOM)31 agosto 2024
Ichibansho Figure JoJo's Bizarre Adventure Jotaro Kujo (Stardust Crusaders) - Tokyo Otaku Mode (TOM)31 agosto 2024 -
 Venda Grande magnético de xadrez de luxo em madeira maciça de xadrez portátil dobrável tabuleiro de xadrez família criativa de crianças, de adultos tabuleiro de jogo ornamentos > Esportes & Entretenimento31 agosto 2024
Venda Grande magnético de xadrez de luxo em madeira maciça de xadrez portátil dobrável tabuleiro de xadrez família criativa de crianças, de adultos tabuleiro de jogo ornamentos > Esportes & Entretenimento31 agosto 2024 -
Battlefield 2042 Open Beta impressions: The first taste31 agosto 2024


