Exploit — Bash Shellshock Part 1. In September 2014, when a single…, by ka1d0
Por um escritor misterioso
Last updated 02 setembro 2024

In September 2014, when a single security bug in Bash was disclosed there was chaos in the security community. This bug allowed attackers to escalate privileges and execute arbitrary code on a remote…
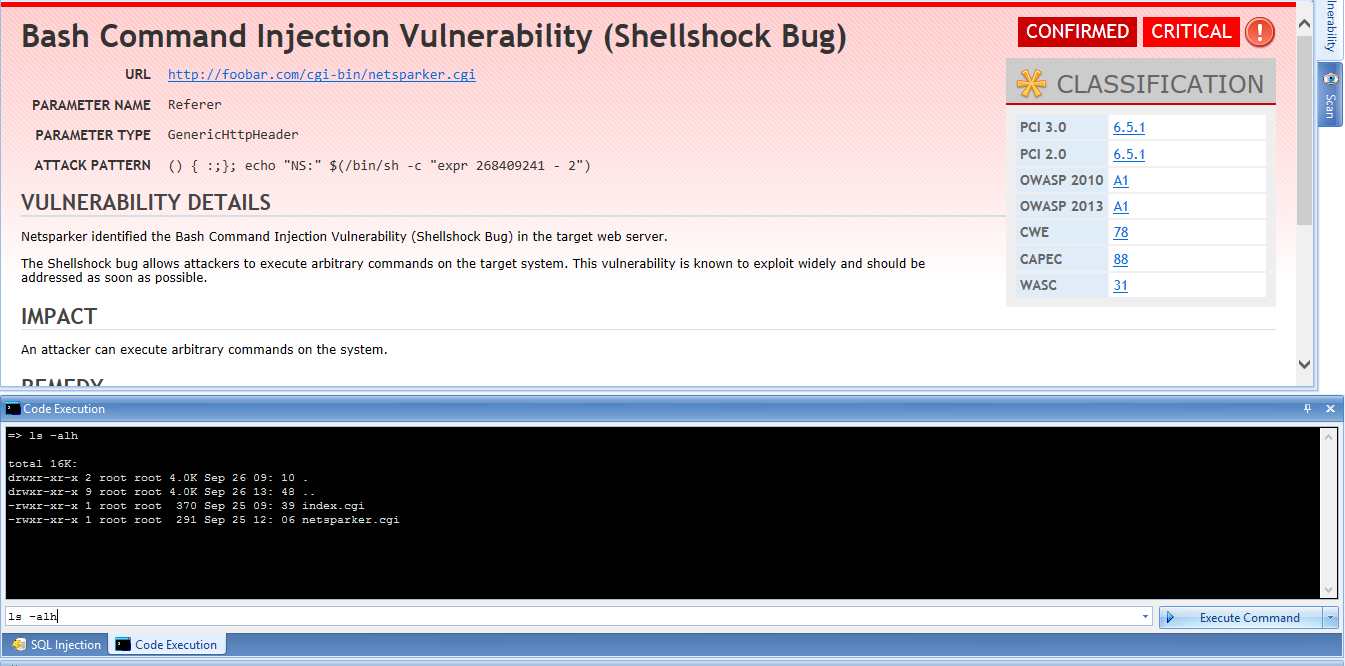
Shellshock Bash Bug Vulnerability Explained
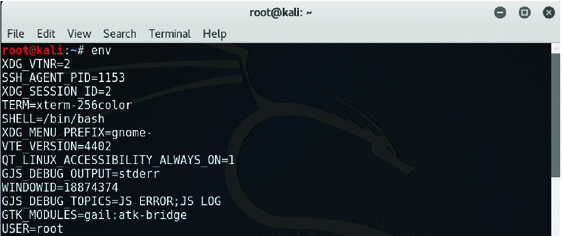
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

Shellshock Bash Bug Vulnerability Explained

Return-Oriented Programming — ROP Chaining, by ka1d0
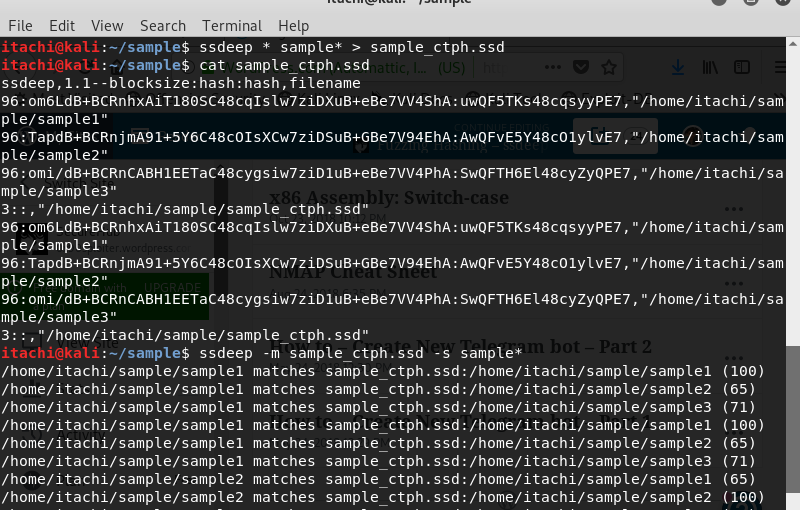
Threat Attribution using ssdeep. We have all used cryptographic hashes…, by ka1d0
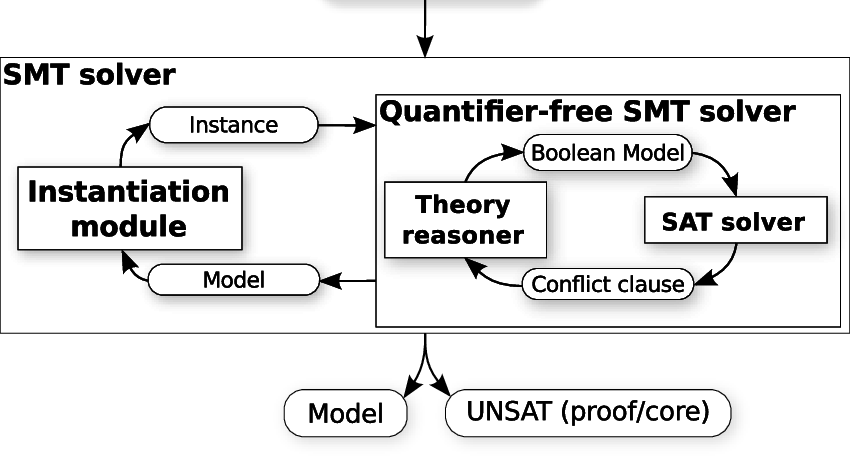
String Deobfuscation using SMT Solver, by ka1d0
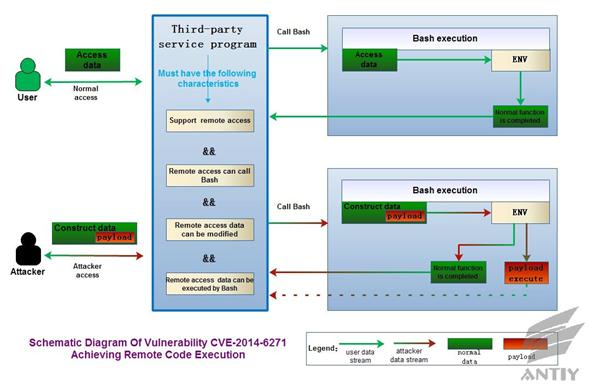
A Comprehensive Analysis on Bash Shellshock (CVE-2014-6271)_V1.53 ——Series One of Bash Shellshock Analysis - Antiy Labs

Threat Intelligence — ste.exe. In the last article about Threat…, by ka1d0
PentesterLab: Learn Web App Pentesting!
Recomendado para você
-
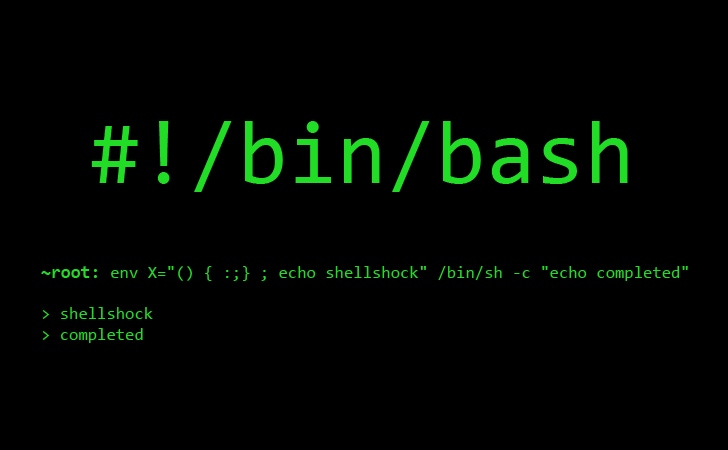 AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems02 setembro 2024
AlienVault Labs: Hackers Can Launch Shellshock Attacks on VoIP Systems02 setembro 2024 -
 Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices02 setembro 2024
Malware Exploits SHELLSHOCK Vulnerability to Hack NAS Devices02 setembro 2024 -
 Shellshock Exploit Hack | Sticker02 setembro 2024
Shellshock Exploit Hack | Sticker02 setembro 2024 -
 Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks02 setembro 2024
Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks02 setembro 2024 -
 Shell Shock Font, Webfont & Desktop02 setembro 2024
Shell Shock Font, Webfont & Desktop02 setembro 2024 -
 Shellshock, aka Bash computer bug, already exploited by hackers02 setembro 2024
Shellshock, aka Bash computer bug, already exploited by hackers02 setembro 2024 -
 Hackers seize Apple computers as Shellshock cyber bug strikes02 setembro 2024
Hackers seize Apple computers as Shellshock cyber bug strikes02 setembro 2024 -
 Shellshock 2 Review - IGN02 setembro 2024
Shellshock 2 Review - IGN02 setembro 2024 -
 What Is Shellshock Bug? - Webber Insurance Services02 setembro 2024
What Is Shellshock Bug? - Webber Insurance Services02 setembro 2024 -
 Are you suffering from ShellShock? - Infosec Partners02 setembro 2024
Are you suffering from ShellShock? - Infosec Partners02 setembro 2024
você pode gostar
-
 26 Times Bobby Hill Was Your Spirit Animal02 setembro 2024
26 Times Bobby Hill Was Your Spirit Animal02 setembro 2024 -
 Bolo De Aniversário Dos Desenhos Animados PNG , Desenho Animado, Bolo De Aniversário, Elemento Png Imagem PNG e PSD Para Download Gratuito02 setembro 2024
Bolo De Aniversário Dos Desenhos Animados PNG , Desenho Animado, Bolo De Aniversário, Elemento Png Imagem PNG e PSD Para Download Gratuito02 setembro 2024 -
 4K AI-Generated Batman Wallpaper for Your Phone02 setembro 2024
4K AI-Generated Batman Wallpaper for Your Phone02 setembro 2024 -
 Pokémon Kangaskhan GX - SM188 - Promo Sun & Moon Promos Mint Jumbo + Regular02 setembro 2024
Pokémon Kangaskhan GX - SM188 - Promo Sun & Moon Promos Mint Jumbo + Regular02 setembro 2024 -
 Read Megami-Ryou No Ryoubo-Kun. Chapter 8 - Mangadex02 setembro 2024
Read Megami-Ryou No Ryoubo-Kun. Chapter 8 - Mangadex02 setembro 2024 -
 F.K. RADNIČKI SOMBOR 1912, Serbian professional football club, vintage flag !02 setembro 2024
F.K. RADNIČKI SOMBOR 1912, Serbian professional football club, vintage flag !02 setembro 2024 -
 Botafogo x Palmeiras: gato 'vidente' revela quem vencerá jogo decisivo02 setembro 2024
Botafogo x Palmeiras: gato 'vidente' revela quem vencerá jogo decisivo02 setembro 2024 -
 Guarda-redes Nakamura renova com Portimonense e fica com cláusula02 setembro 2024
Guarda-redes Nakamura renova com Portimonense e fica com cláusula02 setembro 2024 -
 Netflix e outros streamings podem passar por mudança no Brasil; entenda – Money Times02 setembro 2024
Netflix e outros streamings podem passar por mudança no Brasil; entenda – Money Times02 setembro 2024 -
 Arifureta Shokugyou de Sekai Saikyou Especiales Capitulo 1 Sub02 setembro 2024
Arifureta Shokugyou de Sekai Saikyou Especiales Capitulo 1 Sub02 setembro 2024