SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 07 julho 2024

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

How Hackers Are “Blending In” to Evade Detection

Malware - Wikipedia

SILKLOADER: How Hackers Evade Detection

hacking news, Breaking Cybersecurity News

Simjacker

Hackread - Latest Cybersecurity News, Press Releases & Technology Today

Chinese Silkloader cyber attack tool falls into Russian hands

Windows Red Team Defense Evasion Techniques - HackerSploit Blog

Spixnet - Instagram fined €405m over children's data privacy

Chinese hackers use new custom backdoor to evade detection
Recomendado para você
-
Evade-script/script at main · Lux11111111/Evade-script · GitHub07 julho 2024
-
![OP Evade Script GUI [FREE]](https://vapouryt.co.uk/wp-content/uploads/2022/09/evade-script.jpg) OP Evade Script GUI [FREE]07 julho 2024
OP Evade Script GUI [FREE]07 julho 2024 -
 Snippet of Server-side script generated by ChatGPT to evade07 julho 2024
Snippet of Server-side script generated by ChatGPT to evade07 julho 2024 -
 New ESXiArgs ransomware variant can evade CISA's recovery script07 julho 2024
New ESXiArgs ransomware variant can evade CISA's recovery script07 julho 2024 -
 Enums. Using enums are a really useful way to…07 julho 2024
Enums. Using enums are a really useful way to…07 julho 2024 -
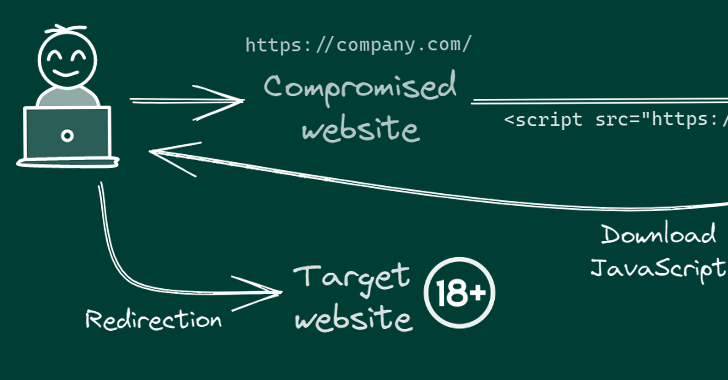 Malicious Python Package Uses Unicode Trickery to Evade Detection07 julho 2024
Malicious Python Package Uses Unicode Trickery to Evade Detection07 julho 2024 -
 Obsidian Giant, Evolution Evade Wiki07 julho 2024
Obsidian Giant, Evolution Evade Wiki07 julho 2024 -
 evade fly script|TikTok Search07 julho 2024
evade fly script|TikTok Search07 julho 2024 -
Sophos - NEW from SophosLabs: AMSI bypasses remain tricks of the07 julho 2024
-
![Desapego Games - League of Legends (LOL) > [PROMOÇÃO] SCRIPT](https://desapegogames.com.br/assets/site/imagens/anuncios/2022/11/01/a69fefbdd4d72ba0922dbaaa065f39fa.jpg) Desapego Games - League of Legends (LOL) > [PROMOÇÃO] SCRIPT07 julho 2024
Desapego Games - League of Legends (LOL) > [PROMOÇÃO] SCRIPT07 julho 2024
você pode gostar
-
 PELA ESTRELA tsukiyama - 49: Eu nunca vou - Wattpad07 julho 2024
PELA ESTRELA tsukiyama - 49: Eu nunca vou - Wattpad07 julho 2024 -
 Watch To LOVE-Ru season 3 episode 3 streaming online07 julho 2024
Watch To LOVE-Ru season 3 episode 3 streaming online07 julho 2024 -
the rumors are true… we have an ambassador program 🎉 this weekend all ambassadors will receive double points on all purchases and…07 julho 2024
-
 Avatar: The Four Nations: 1.1 Preview news - Mod DB07 julho 2024
Avatar: The Four Nations: 1.1 Preview news - Mod DB07 julho 2024 -
 Women's Breton Rouge Traditional Guernsey Jumper07 julho 2024
Women's Breton Rouge Traditional Guernsey Jumper07 julho 2024 -
 Console Nintendo Wii U Usado07 julho 2024
Console Nintendo Wii U Usado07 julho 2024 -
 Mako Mermaids : Season 1 (Box Set, DVD, 2013) for sale online07 julho 2024
Mako Mermaids : Season 1 (Box Set, DVD, 2013) for sale online07 julho 2024 -
 Shiny Rayquaza, Wiki07 julho 2024
Shiny Rayquaza, Wiki07 julho 2024 -
 Werewolf by Night (2022) directed by Michael Giacchino • Reviews07 julho 2024
Werewolf by Night (2022) directed by Michael Giacchino • Reviews07 julho 2024 -
 como simplificar a raiz de 53?07 julho 2024
como simplificar a raiz de 53?07 julho 2024

