SSH Passwd, PDF, Cyberwarfare
Por um escritor misterioso
Last updated 06 setembro 2024


PDF) Teaching pentesting to social sciences students using experiential learning techniques to improve attitudes towards possible cybersecurity careers

Implementing and evaluating a GDPR-compliant open-source SIEM solution - ScienceDirect

Implications of Misuse and Cyber Security.pdf

Xiologix Security overview - Tualatin, Oregon, United States of America

Password-Less SSH Setup: Getting Started, PDF, Superuser

PDF] A Study of Passwords and Methods Used in Brute-Force SSH Attacks

SSH Passwd, PDF, Cyberwarfare

New Android Malware Steals Crypto Credentials Using uses OCR

Password-Stealing Commits Disguised as Dependabot Contributions Target GitHub Repositories
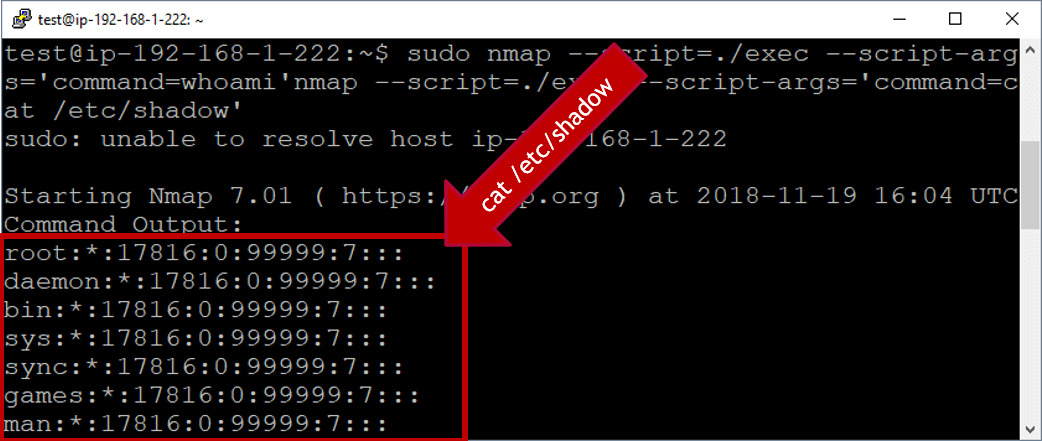
Linux Hacking Case Studies Part 4: Sudo Horror Stories
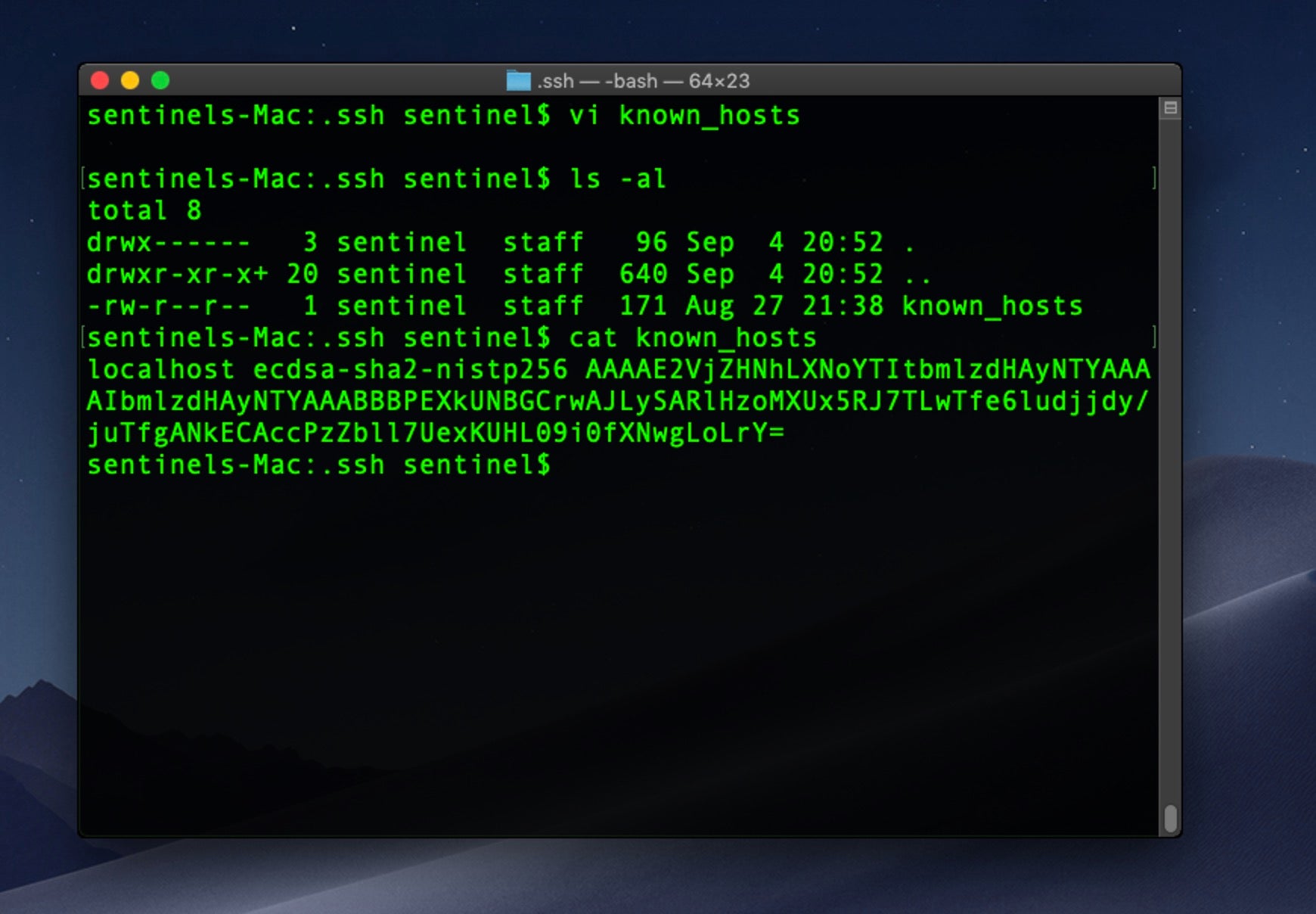
macOS Incident Response Part 3: System Manipulation - SentinelLabs

Black Hills Information Security
Recomendado para você
-
Untitled06 setembro 2024
-
![Stream 1234567890-=qwertyuioppasdfgghjkl;'']\[zxcvbnm,./ music](https://i1.sndcdn.com/avatars-000411794346-ljb36l-t500x500.jpg) Stream 1234567890-=qwertyuioppasdfgghjkl;'']\[zxcvbnm,./ music06 setembro 2024
Stream 1234567890-=qwertyuioppasdfgghjkl;'']\[zxcvbnm,./ music06 setembro 2024 -
 gummy bear06 setembro 2024
gummy bear06 setembro 2024 -
 Qwertyuiop06 setembro 2024
Qwertyuiop06 setembro 2024 -
 Qwertyuiopasdfghjklzxcvbnm06 setembro 2024
Qwertyuiopasdfghjklzxcvbnm06 setembro 2024 -
 Poi - Launch Trailer06 setembro 2024
Poi - Launch Trailer06 setembro 2024 -
password-strength/data/common-passwords.txt at master · tests06 setembro 2024
-
40k HQ Combo @ranjeetsarmah06 setembro 2024
-
 Password Dico 4 – SecPadawan06 setembro 2024
Password Dico 4 – SecPadawan06 setembro 2024 -
![1234567890-=qwertyuiop[]\asdfghjkl;'zxcvbnm,./?><](https://www.tynker.com/projects/screenshot/604138b40c7029648225b198/1234567890-qwertyuiop-asdfghjkl-zxcvbnm-mnbvcxz-lkjhgfdsa-poiuytrewq.png) 1234567890-=qwertyuiop[]\asdfghjkl;'zxcvbnm,./?><06 setembro 2024
1234567890-=qwertyuiop[]\asdfghjkl;'zxcvbnm,./?><06 setembro 2024
você pode gostar
-
format(webp)) Kaguya-sama Season 3 Shows Off Shirogane and Fujiwara's Rap Skills06 setembro 2024
Kaguya-sama Season 3 Shows Off Shirogane and Fujiwara's Rap Skills06 setembro 2024 -
 Bolo decorado cobertura de chantily e frutas – Ateliê do Bolo Maceió06 setembro 2024
Bolo decorado cobertura de chantily e frutas – Ateliê do Bolo Maceió06 setembro 2024 -
 Qué equipos de la Liga MX tienen más títulos y finales disputadas en el siglo XXI hasta el 2022?06 setembro 2024
Qué equipos de la Liga MX tienen más títulos y finales disputadas en el siglo XXI hasta el 2022?06 setembro 2024 -
 O seu palpit de sorte!06 setembro 2024
O seu palpit de sorte!06 setembro 2024 -
 WATCH: 'Messi's World Cup: The Rise of a Legend' trailer & release06 setembro 2024
WATCH: 'Messi's World Cup: The Rise of a Legend' trailer & release06 setembro 2024 -
Kiyoe on X: Knight's & Magic vol 9 Illustrations / X06 setembro 2024
-
 Best Bob Marley Love Songs: 20 Tracks To Satisfy Your Soul06 setembro 2024
Best Bob Marley Love Songs: 20 Tracks To Satisfy Your Soul06 setembro 2024 -
 Crítica Battle Angel Alita - Volumes 1 a 3 - Plano Crítico06 setembro 2024
Crítica Battle Angel Alita - Volumes 1 a 3 - Plano Crítico06 setembro 2024 -
 Bahia x Atlético-MG Ao Vivo: onde assistir online e na TV ao jogo06 setembro 2024
Bahia x Atlético-MG Ao Vivo: onde assistir online e na TV ao jogo06 setembro 2024 -
Paradise City - Guns N' Roses #fyp #gunsnroses #guitar #80s #rock06 setembro 2024



