Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 01 setembro 2024
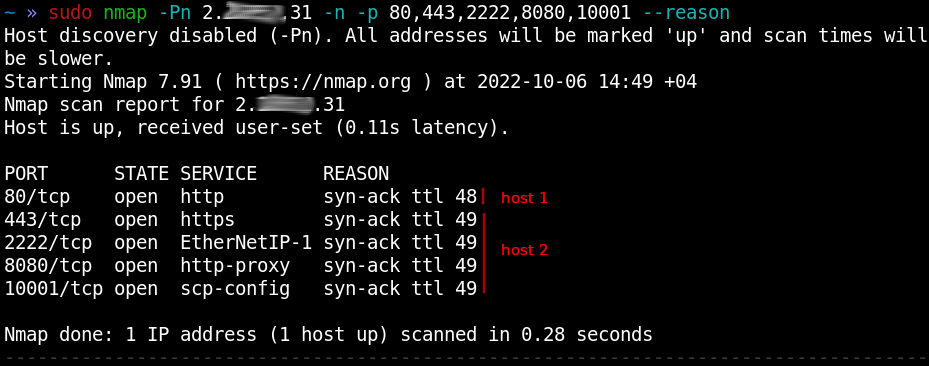

Kung fu enumeration. Data collection in attacked systems – HackMag
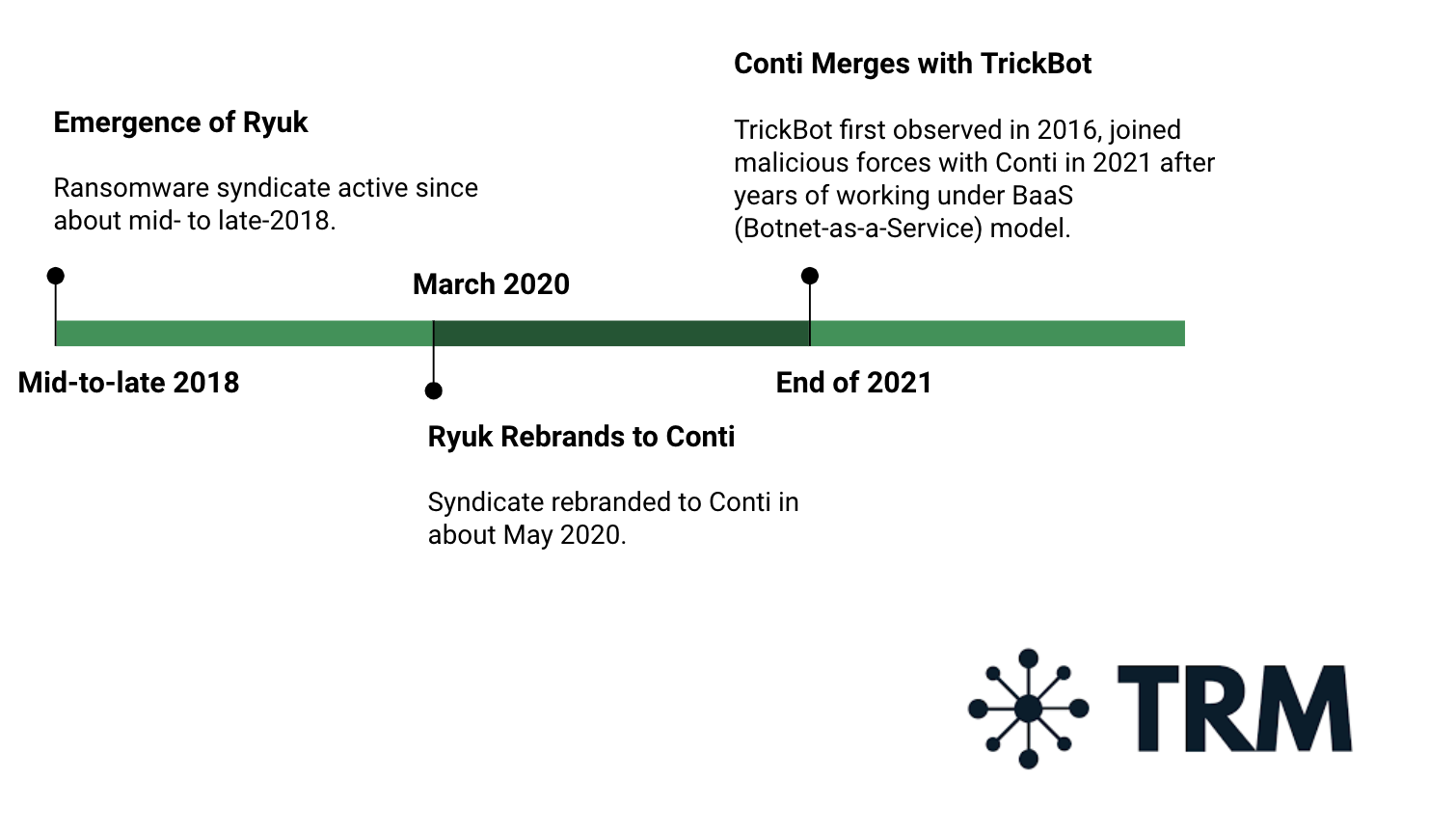
TRM Analysis Corroborates Suspected Ties Between Conti and Ryuk

Subterfuge (Man-in-the-Middle Attack Framework) - Hacking Articles

Machine Learning under Malware Attack

Web-Attack-Cheat-Sheet. Discovering, by Hasanka Amarasinghe
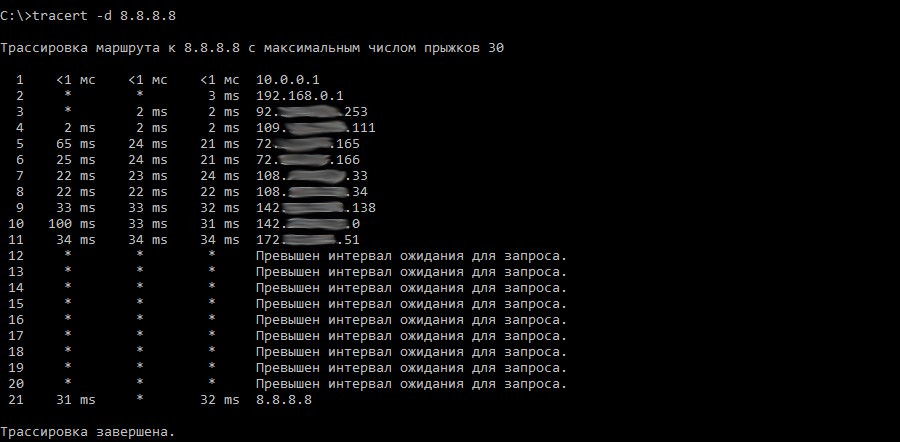
Kung fu enumeration. Data collection in attacked systems – HackMag

HACKMAGEDDON – Information Security Timelines and Statistics
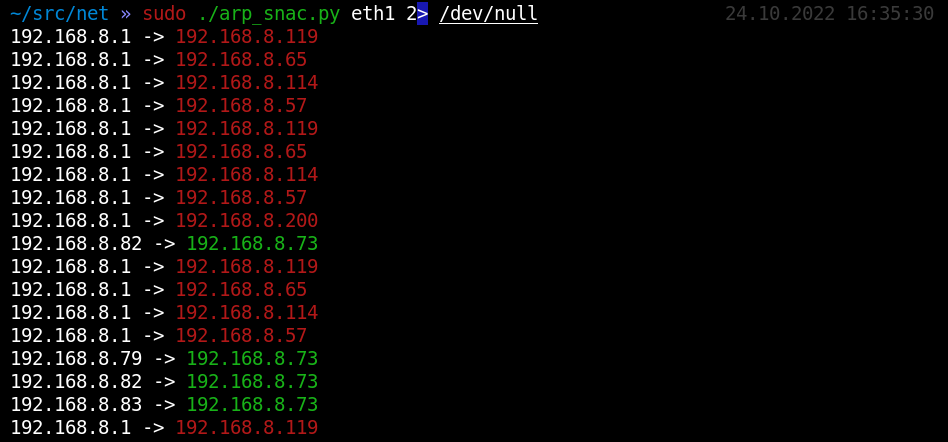
Kung fu enumeration. Data collection in attacked systems – HackMag
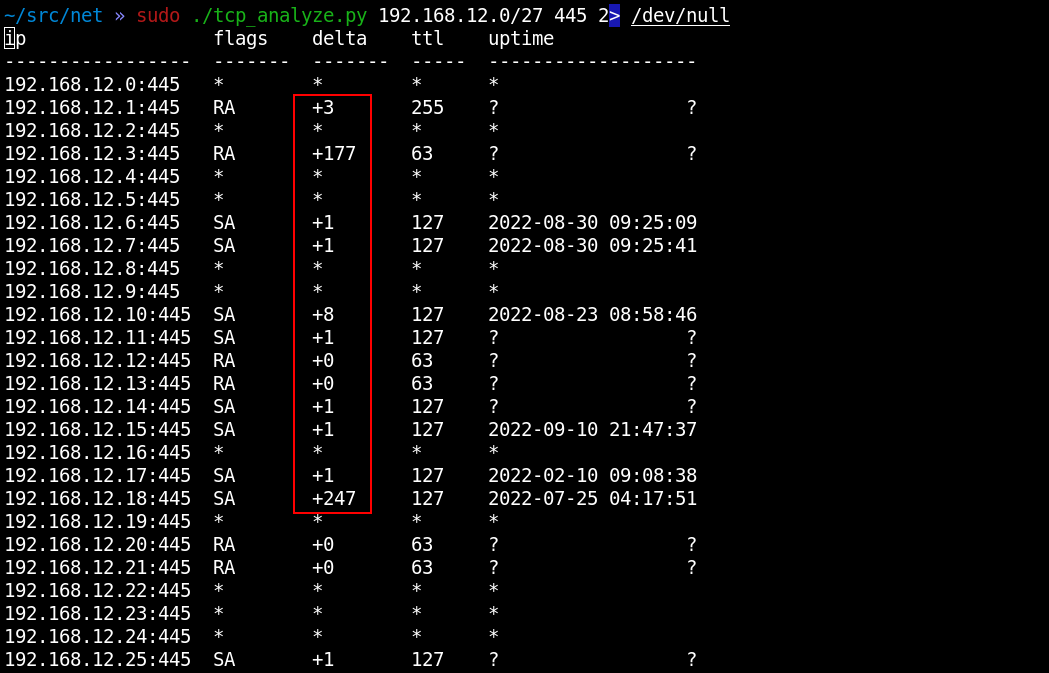
Kung fu enumeration. Data collection in attacked systems – HackMag
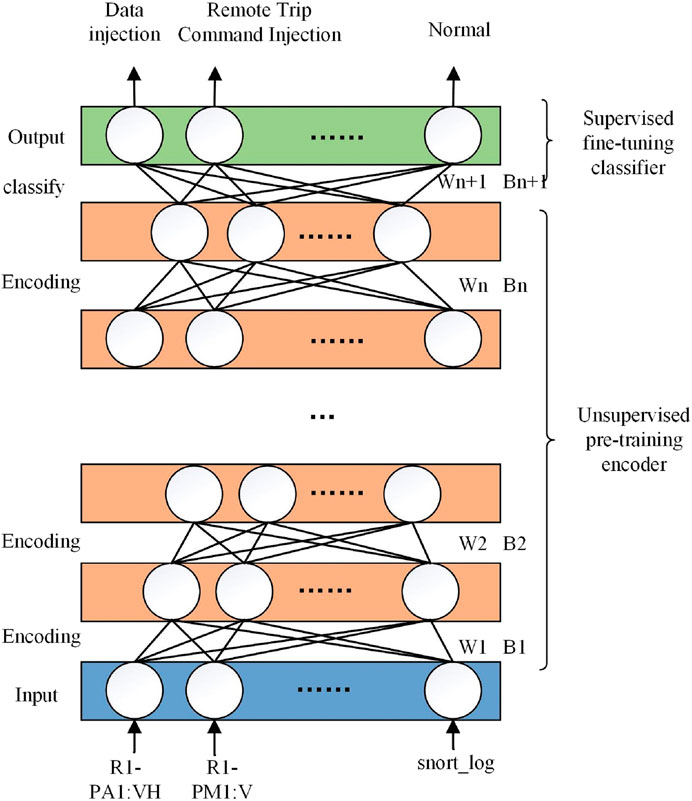
Frontiers False Data Injection Attack Detection in Power Systems

Hakka Fist Snapping Claws - Technique and Applications - Kung Fu
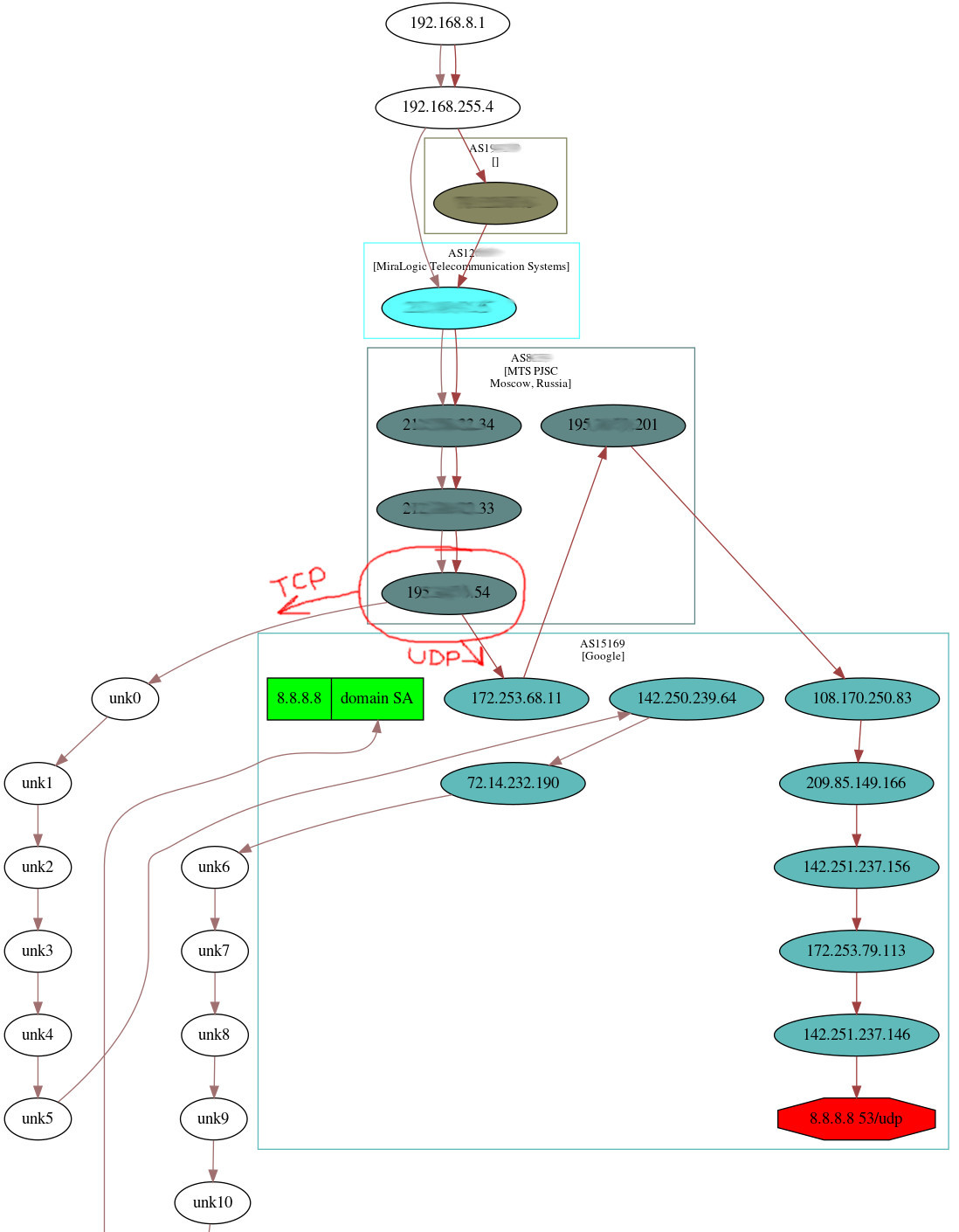
Kung fu enumeration. Data collection in attacked systems – HackMag
Recomendado para você
-
 The One Club Announces 29 Global Winners For Young Guns 2101 setembro 2024
The One Club Announces 29 Global Winners For Young Guns 2101 setembro 2024 -
 Category:Low Effort, SCP Fanon Wiki01 setembro 2024
Category:Low Effort, SCP Fanon Wiki01 setembro 2024 -
 NFT Whale Alert on X: Lonely Alien Space Club 10001 bought for Ξ60 ($192133.20) Rare Traits: OS: FUR_COAT_PURPLE - 1.94% BODY: GALAXY_BLUE - 0.89% HAT: DJ_HELMET - 0.44% / X01 setembro 2024
NFT Whale Alert on X: Lonely Alien Space Club 10001 bought for Ξ60 ($192133.20) Rare Traits: OS: FUR_COAT_PURPLE - 1.94% BODY: GALAXY_BLUE - 0.89% HAT: DJ_HELMET - 0.44% / X01 setembro 2024 -
 SCP--KARMA:. by XenomorphicDragon on DeviantArt01 setembro 2024
SCP--KARMA:. by XenomorphicDragon on DeviantArt01 setembro 2024 -
 Snarferman01 setembro 2024
Snarferman01 setembro 2024 -
SCP - 10001 (@JKweesley32757) / X01 setembro 2024
-
 Women's and Girls' Running Shoes, Clothing and Gear01 setembro 2024
Women's and Girls' Running Shoes, Clothing and Gear01 setembro 2024 -
Sapiens Grimsby01 setembro 2024
-
poppies: Blue Water Health01 setembro 2024
-
 Muerte by Arfaxad, dark Paintings for sale, direct from the artist01 setembro 2024
Muerte by Arfaxad, dark Paintings for sale, direct from the artist01 setembro 2024
você pode gostar
-
 Mateus Asato toca com Bruno Mars e Anderson .Paak no Grammy01 setembro 2024
Mateus Asato toca com Bruno Mars e Anderson .Paak no Grammy01 setembro 2024 -
 Poster Sono Bisque Doll Wa Koi Wo Suru 5 Sticker for Sale by Kami-Anime01 setembro 2024
Poster Sono Bisque Doll Wa Koi Wo Suru 5 Sticker for Sale by Kami-Anime01 setembro 2024 -
 Como fazer bolo de milho verde cremoso01 setembro 2024
Como fazer bolo de milho verde cremoso01 setembro 2024 -
 CONSEGUI A TRANSFORMAÇÃO SECRETA DO TAILS NO ROBLOX!! (Sonic Speed Simulator)01 setembro 2024
CONSEGUI A TRANSFORMAÇÃO SECRETA DO TAILS NO ROBLOX!! (Sonic Speed Simulator)01 setembro 2024 -
 Cabo Verde voltou a perder nas olimpíadas de xadrez de Chenai na Índia01 setembro 2024
Cabo Verde voltou a perder nas olimpíadas de xadrez de Chenai na Índia01 setembro 2024 -
 OS 10 MELHORES JOGOS MULTIPLAYER ONLINE PARA JOGAR COM AMIGOS Android 202201 setembro 2024
OS 10 MELHORES JOGOS MULTIPLAYER ONLINE PARA JOGAR COM AMIGOS Android 202201 setembro 2024 -
 Friday the 13th : The game APK for Android Download01 setembro 2024
Friday the 13th : The game APK for Android Download01 setembro 2024 -
![For Beginners] How to paint your character's hair easily](https://medibangpaint.com/wp-content/uploads/2021/06/10-1.jpg) For Beginners] How to paint your character's hair easily01 setembro 2024
For Beginners] How to paint your character's hair easily01 setembro 2024 -
blox logo - Roblox01 setembro 2024
-
 Independiente de Chivilcoy segura a vantagem sobre o Camioneros e01 setembro 2024
Independiente de Chivilcoy segura a vantagem sobre o Camioneros e01 setembro 2024



