Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 31 agosto 2024

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Unsupervised Anomaly Detectors to Detect Intrusions in the Current
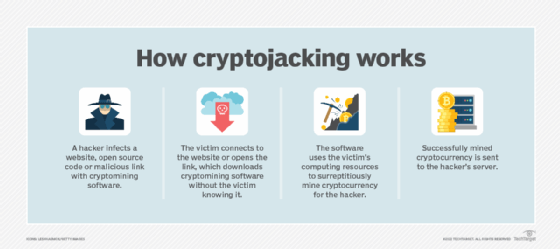
What is Cryptojacking? Detection and Preventions Techniques

Austreme Discovers Crypto-jacking Software in Merchant Sites

Cryptojacking Miners for the first time on the Microsoft Store

What is Cryptojacking. Criminals are now using ransomware-like

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

4 things you should know about Cryptojacking

ENISA's Threat Landscape and the Effect of Ransomware

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

Defeat Crypto jacking with Decryption and Inspection IT Voice

The Anomali Blog
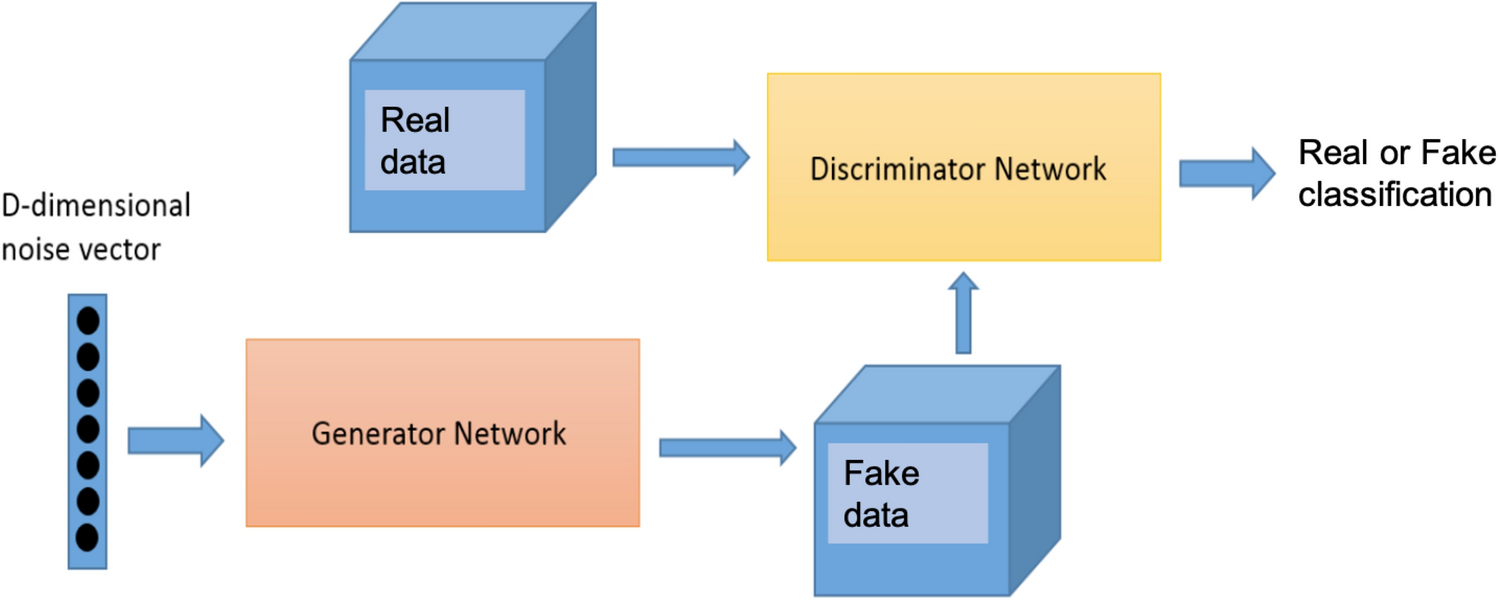
Synthetic flow-based cryptomining attack generation through
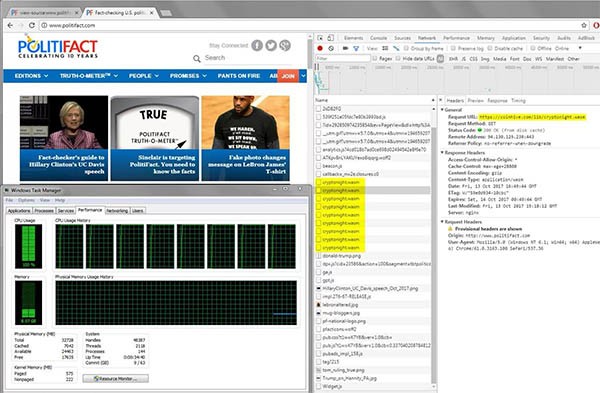
How Hackers Use Cryptojacking Malware to Take Over Computers to
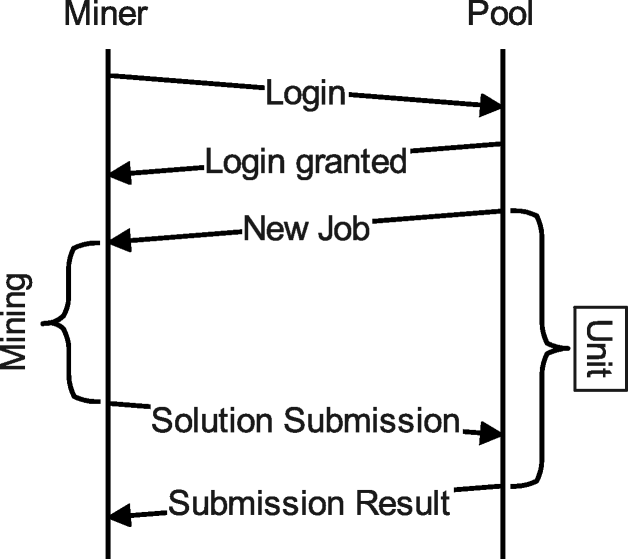
Detection of illicit cryptomining using network metadata
Recomendado para você
-
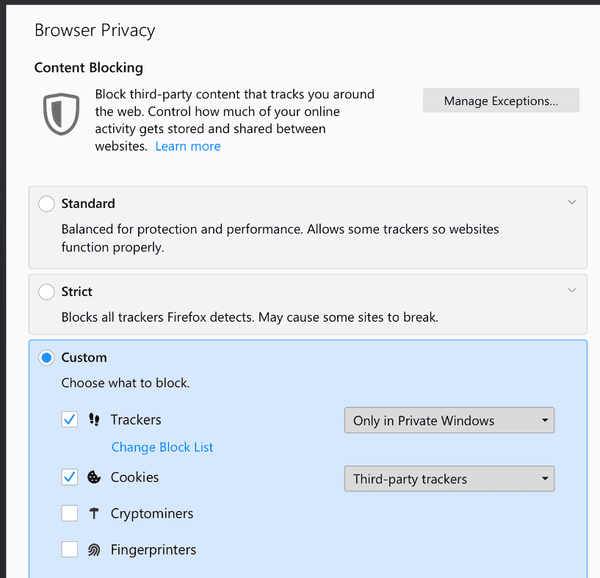 Firefox 67: Cryptocurrency miners and Fingerprinters protection31 agosto 2024
Firefox 67: Cryptocurrency miners and Fingerprinters protection31 agosto 2024 -
 Deeper Network Connect PICO Crypto Miner DPN/VPN + Wifi Adapter IN HAND - NEW31 agosto 2024
Deeper Network Connect PICO Crypto Miner DPN/VPN + Wifi Adapter IN HAND - NEW31 agosto 2024 -
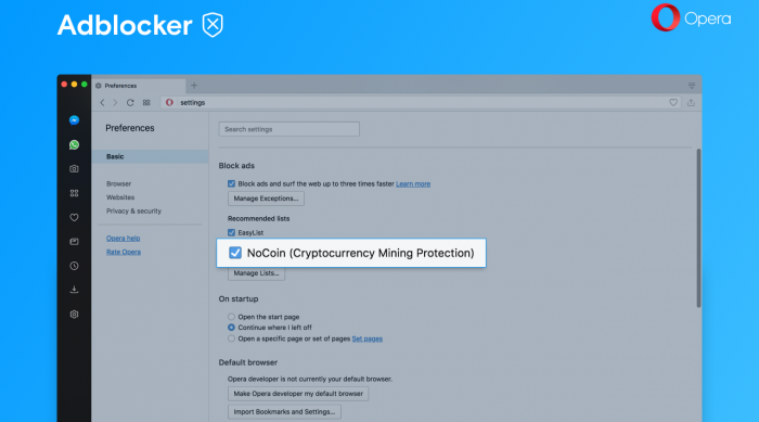 Opera adds anti-cryptocurrency mining feature to mobile browsers31 agosto 2024
Opera adds anti-cryptocurrency mining feature to mobile browsers31 agosto 2024 -
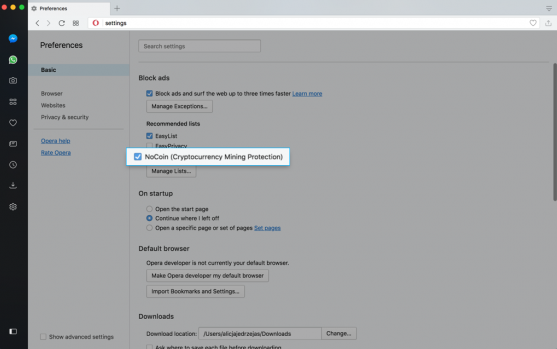 Opera 50 Beta Version to Come with Cryptocurrency Mining Blocker31 agosto 2024
Opera 50 Beta Version to Come with Cryptocurrency Mining Blocker31 agosto 2024 -
 Stablecoin Issuer Tether (USDT/BTC) Wants to Become a Major Bitcoin Miner - Bloomberg31 agosto 2024
Stablecoin Issuer Tether (USDT/BTC) Wants to Become a Major Bitcoin Miner - Bloomberg31 agosto 2024 -
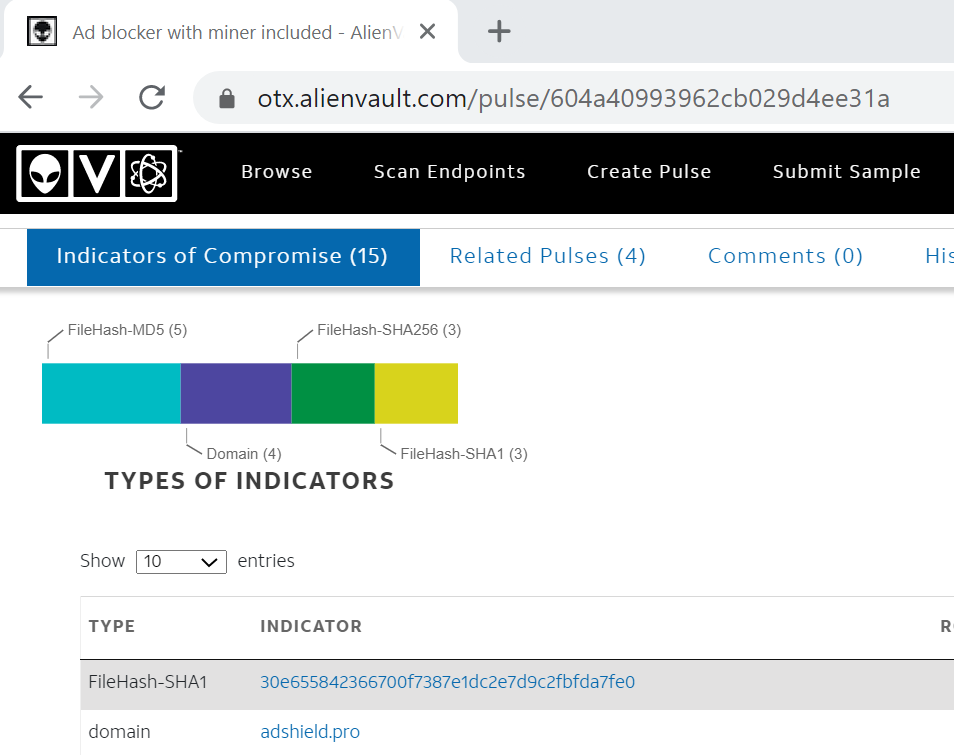 Malware Detection31 agosto 2024
Malware Detection31 agosto 2024 -
 STL file Fantasy Football - Dwarf Blocker 02・Template to download31 agosto 2024
STL file Fantasy Football - Dwarf Blocker 02・Template to download31 agosto 2024 -
 AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock31 agosto 2024
AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock31 agosto 2024 -
 Men's Basketball - UTEP Miners31 agosto 2024
Men's Basketball - UTEP Miners31 agosto 2024 -
 How to stop websites from using your computer to mine Bitcoin (and more) - CNET31 agosto 2024
How to stop websites from using your computer to mine Bitcoin (and more) - CNET31 agosto 2024
você pode gostar
-
 ALTRONIC TEI-01 MC TEI-TEMPO 30S MULTI FUNCTION TIME RELAY31 agosto 2024
ALTRONIC TEI-01 MC TEI-TEMPO 30S MULTI FUNCTION TIME RELAY31 agosto 2024 -
 Cursed Emojis: Unleash Your True Self 🤬 With The Art Of Emojis31 agosto 2024
Cursed Emojis: Unleash Your True Self 🤬 With The Art Of Emojis31 agosto 2024 -
 Shokugeki no Souma: Ni no Sara (Food Wars! S2) Review – The31 agosto 2024
Shokugeki no Souma: Ni no Sara (Food Wars! S2) Review – The31 agosto 2024 -
 Confira todos animes dublados em português disponíveis aqui na31 agosto 2024
Confira todos animes dublados em português disponíveis aqui na31 agosto 2024 -
 The Outlast Trials Free Download FULL Version PC Game31 agosto 2024
The Outlast Trials Free Download FULL Version PC Game31 agosto 2024 -
 Rick Roll Fail - 9GAG31 agosto 2024
Rick Roll Fail - 9GAG31 agosto 2024 -
 Roblox Imagens aleatórias, Fotos, Roblox31 agosto 2024
Roblox Imagens aleatórias, Fotos, Roblox31 agosto 2024 -
 Gate jieitai kanochi nite kaku tatakaeri, Wiki31 agosto 2024
Gate jieitai kanochi nite kaku tatakaeri, Wiki31 agosto 2024 -
 Happy Color: Color by Number v2.14.4 Apk Mod (Dicas Infinitas31 agosto 2024
Happy Color: Color by Number v2.14.4 Apk Mod (Dicas Infinitas31 agosto 2024 -
 The Master of Ragnarok & Blesser of Einherjar (Hyakuren no Haou to Seiyaku no Valkyria) 21 (Light Novel) – Japanese Book Store31 agosto 2024
The Master of Ragnarok & Blesser of Einherjar (Hyakuren no Haou to Seiyaku no Valkyria) 21 (Light Novel) – Japanese Book Store31 agosto 2024