Enforcing SBOMs through the Linux kernel with eBPF and IMA
Por um escritor misterioso
Last updated 10 julho 2024


Diane Mueller on LinkedIn: Linux has over 3% of the desktop market

EdgeBit on LinkedIn: We're excited to be part of the Y Combinator
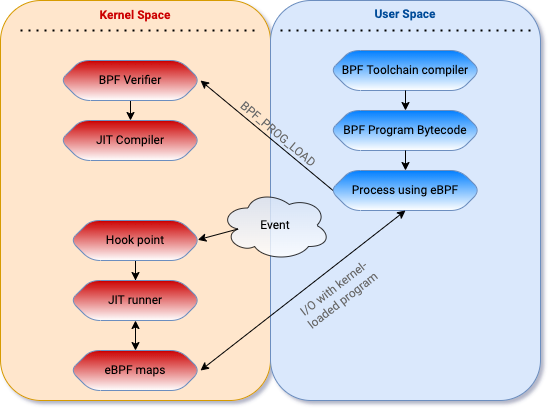
On Bypassing eBPF Security Monitoring · Doyensec's Blog
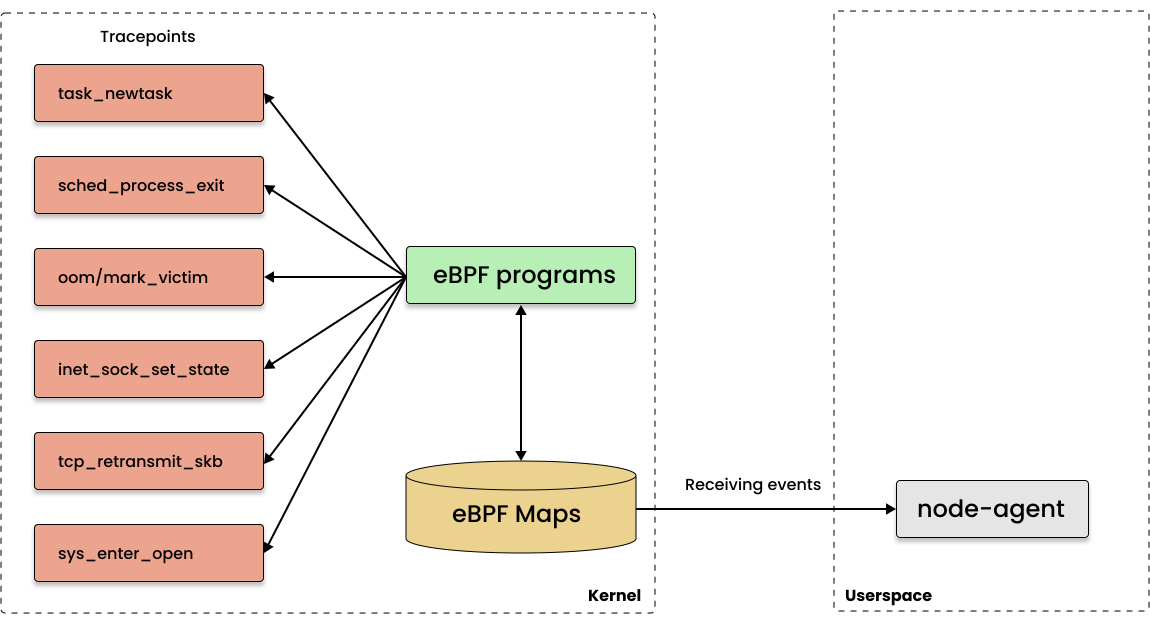
The current state of eBPF portability, Blog

Advanced Persistent Threat Techniques Used in Container Attacks

Tetragon adds visibility to Kubernetes with open-source runtime
/presentations/facebook-google-bpf-linux-kernel/en/slides/sl5-1586362920056.jpg)
eBPF - Rethinking the Linux Kernel
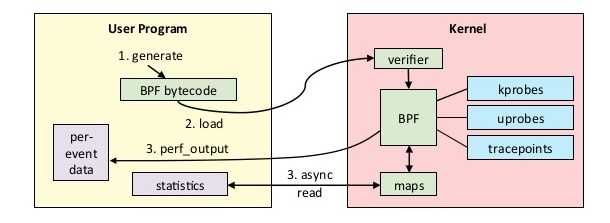
Debugging with eBPF Part 1: Tracing Go function arguments in prod

Discover the Basics of Telemetry - Metrics What You Need to Know

Container Isolation: Is a Container a Security Boundary?
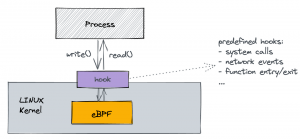
Get started with eBPF using BumbleBee
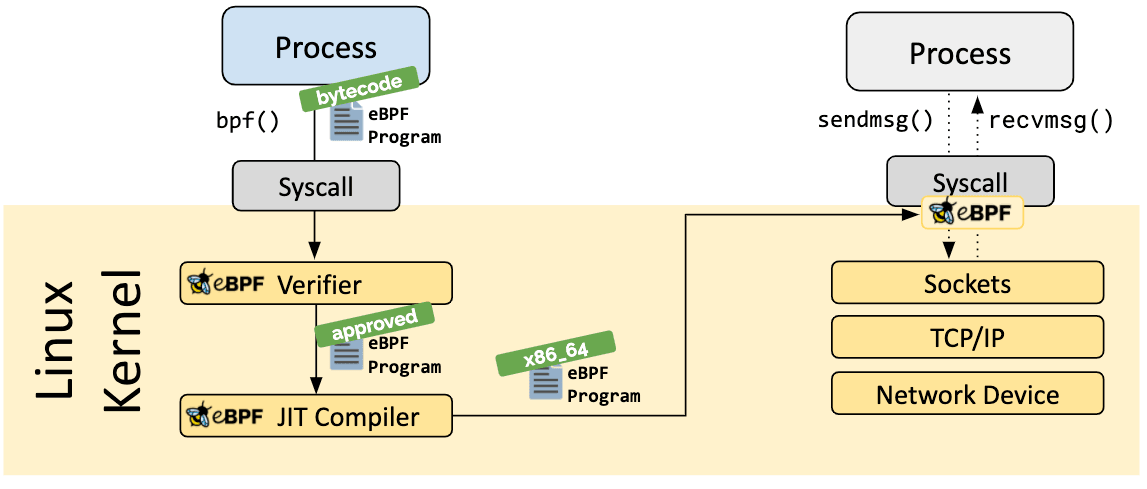
What is eBPF? An Introduction and Deep Dive into the eBPF Technology
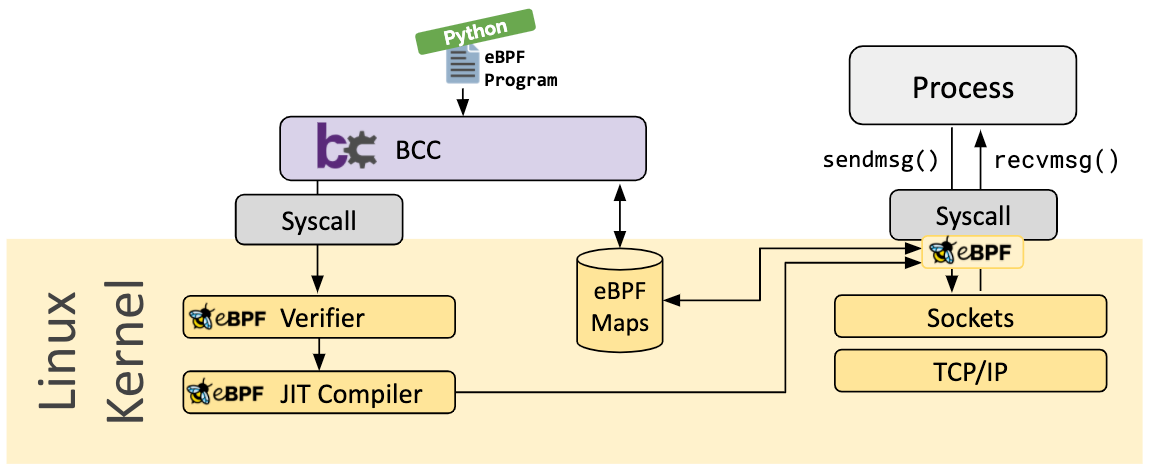
What is eBPF? – eBPF
Cilium 1.13 - Gateway API, mTLS datapath, Service Mesh, BIG TCP
Recomendado para você
-
 Paper Io: Conquer The Virtual World!10 julho 2024
Paper Io: Conquer The Virtual World!10 julho 2024 -
 Paper.io 2 Teams UnbLoCked10 julho 2024
Paper.io 2 Teams UnbLoCked10 julho 2024 -
Download Paper IO 2 - Play with Paper on PC (Emulator) - LDPlayer10 julho 2024
-
 Just Got 100% in Paper.io 2 Teams Mode!! : r/AdvertiseYourVideos10 julho 2024
Just Got 100% in Paper.io 2 Teams Mode!! : r/AdvertiseYourVideos10 julho 2024 -
How to team up in Paper.io - How to team up in Paper.io 210 julho 2024
-
 Which team in Paper.io2 will you be on (Paper.io2 team mode) - Quiz10 julho 2024
Which team in Paper.io2 will you be on (Paper.io2 team mode) - Quiz10 julho 2024 -
 Paper io 2 Walkthrough10 julho 2024
Paper io 2 Walkthrough10 julho 2024 -
 Paper.io 2 - you can opt-out but you can't save your setting. This is not GDPR compliant. : r/assholedesign10 julho 2024
Paper.io 2 - you can opt-out but you can't save your setting. This is not GDPR compliant. : r/assholedesign10 julho 2024 -
 Descarga de la aplicación Paper.io 2 2023 - Gratis - 9Apps10 julho 2024
Descarga de la aplicación Paper.io 2 2023 - Gratis - 9Apps10 julho 2024 -
 Color Pathio Play Now Online for Free10 julho 2024
Color Pathio Play Now Online for Free10 julho 2024
você pode gostar
-
 Spaceman Amphibian Stage10 julho 2024
Spaceman Amphibian Stage10 julho 2024 -
Minecraft Ultimate Ender Dragon Figure by Minecraft at Fleet Farm10 julho 2024
-
 Multiple forms of working memory emerge from synapse–astrocyte interactions in a neuron–glia network model10 julho 2024
Multiple forms of working memory emerge from synapse–astrocyte interactions in a neuron–glia network model10 julho 2024 -
 O GAMBITO DA RAINHA VAI TER 2ª TEMPORADA?10 julho 2024
O GAMBITO DA RAINHA VAI TER 2ª TEMPORADA?10 julho 2024 -
 Stellaris grand strategy space game by Paradox discussy thingy10 julho 2024
Stellaris grand strategy space game by Paradox discussy thingy10 julho 2024 -
 The Very Best Podcasts of 202310 julho 2024
The Very Best Podcasts of 202310 julho 2024 -
 Desenho de princesa com sapo para colorir10 julho 2024
Desenho de princesa com sapo para colorir10 julho 2024 -
 Ousama Ranking - Saison 2 Anime-Sama - Streaming et catalogage d10 julho 2024
Ousama Ranking - Saison 2 Anime-Sama - Streaming et catalogage d10 julho 2024 -
![5 Best 6.5 Grendel Uppers [Hands-On] - Pew Pew Tactical](https://www.pewpewtactical.com/wp-content/uploads/2019/01/atheris100-1024x768.jpg) 5 Best 6.5 Grendel Uppers [Hands-On] - Pew Pew Tactical10 julho 2024
5 Best 6.5 Grendel Uppers [Hands-On] - Pew Pew Tactical10 julho 2024 -
 Yasuke' Trailer: New Look at Netflix's LaKeith Stanfield Anime10 julho 2024
Yasuke' Trailer: New Look at Netflix's LaKeith Stanfield Anime10 julho 2024

