How hackers use idle scans in port scan attacks
Por um escritor misterioso
Last updated 09 setembro 2024
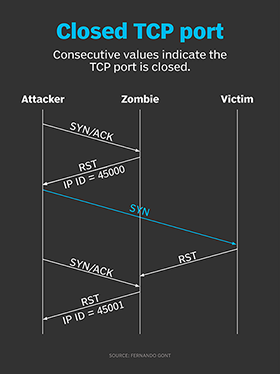
Hackers employ a variety of port scan attacks to gain entry into an enterprise network. Idle scans are a popular method to mask the hacker
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
Hackers exploit port scan attacks to mask their identities before launching an attack. One of their favorites: the idle scan.
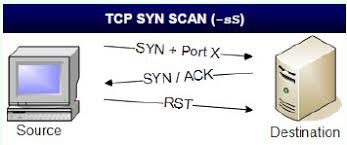
SYN Stealth, XMAS, NULL, IDLE, FIN

Idle scan - Wikipedia
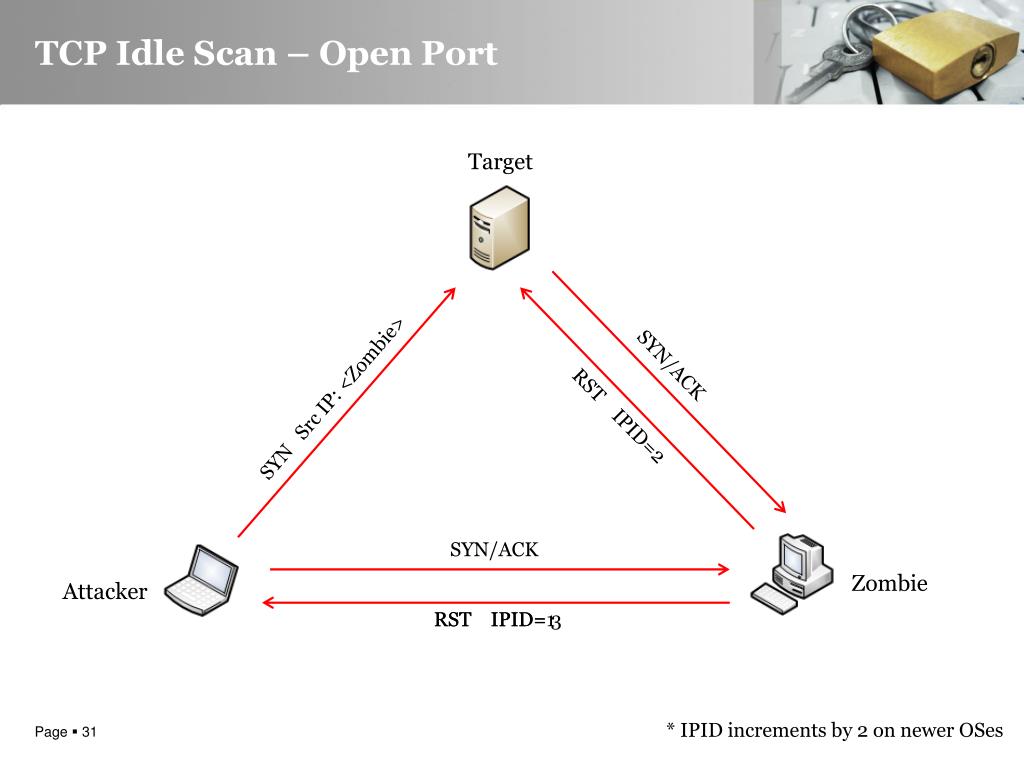
PPT - Advanced Idle Scanning PowerPoint Presentation, free download - ID:5241398

PDF) Surveying Port Scans and Their Detection Methodologies
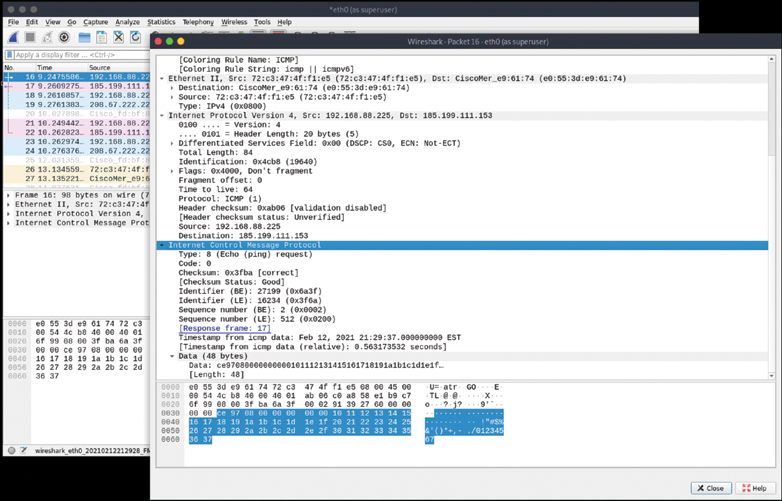
Scanning, Footprinting, Reconnaissance, and Scanning
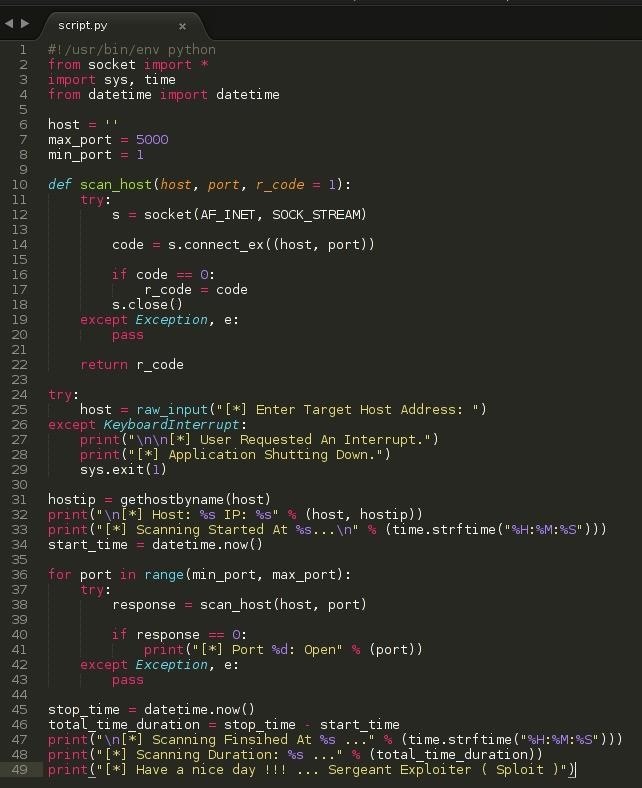
SPLOIT: How to Make a Python Port Scanner « Null Byte :: WonderHowTo
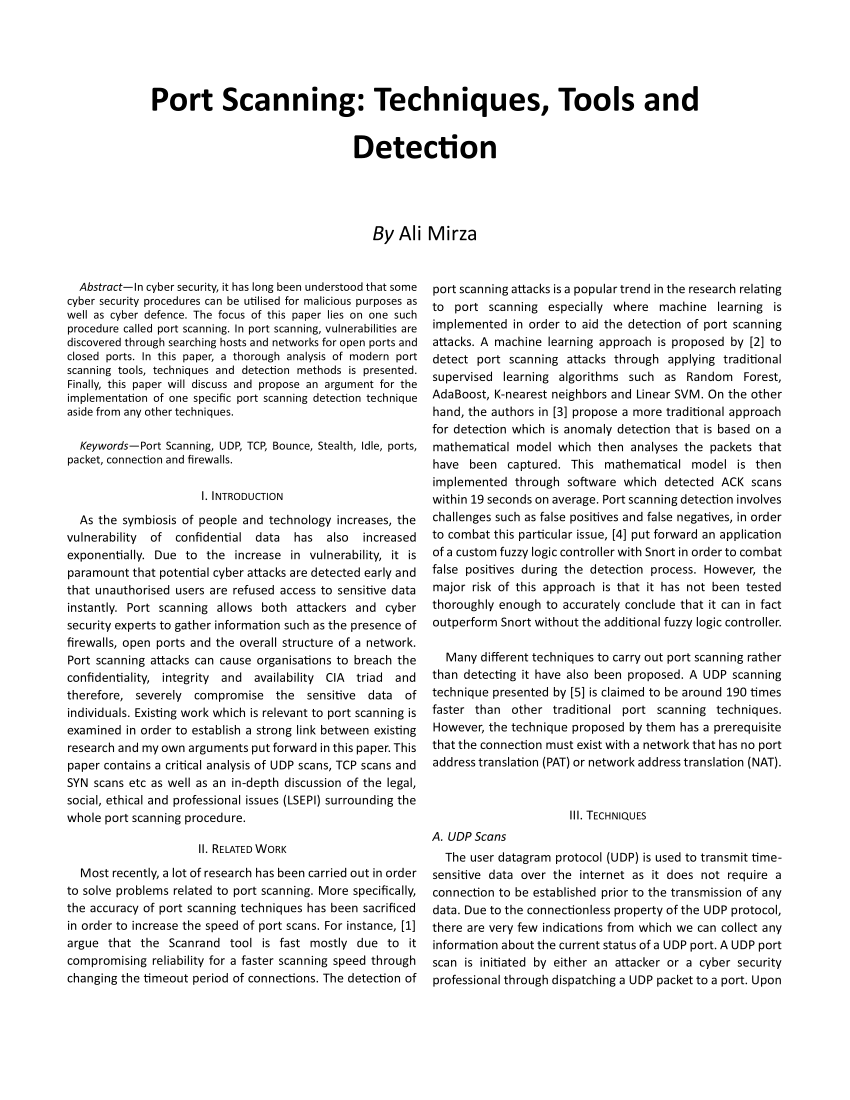
PDF) Port Scanning: Techniques, Tools and Detection
What Is Nmap? A Comprehensive Tutorial For Network Mapping
What Is Nmap? A Comprehensive Tutorial For Network Mapping
What Is Nmap? A Comprehensive Tutorial For Network Mapping
Recomendado para você
-
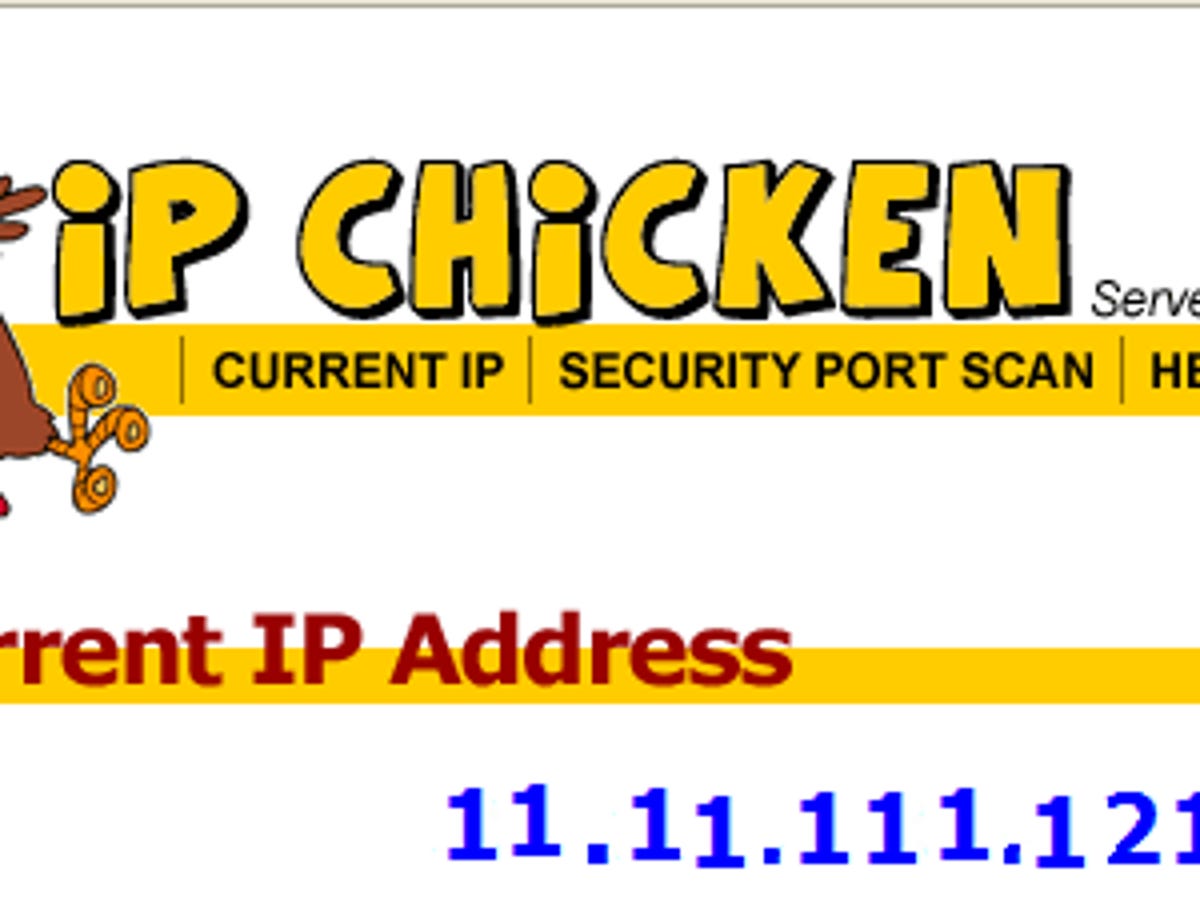 What does your IP address say about you? - CNET09 setembro 2024
What does your IP address say about you? - CNET09 setembro 2024 -
ipchicken.com Traffic Analytics, Ranking Stats & Tech Stack09 setembro 2024
-
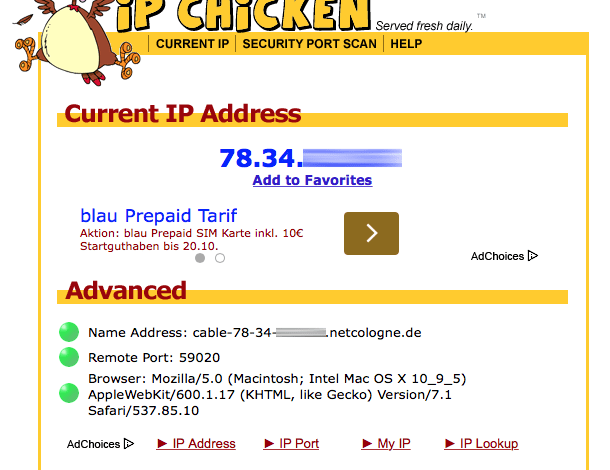 Read own IP address and check anonymization09 setembro 2024
Read own IP address and check anonymization09 setembro 2024 -
 How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 setembro 2024
How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey09 setembro 2024 -
 Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey09 setembro 2024
Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey09 setembro 2024 -
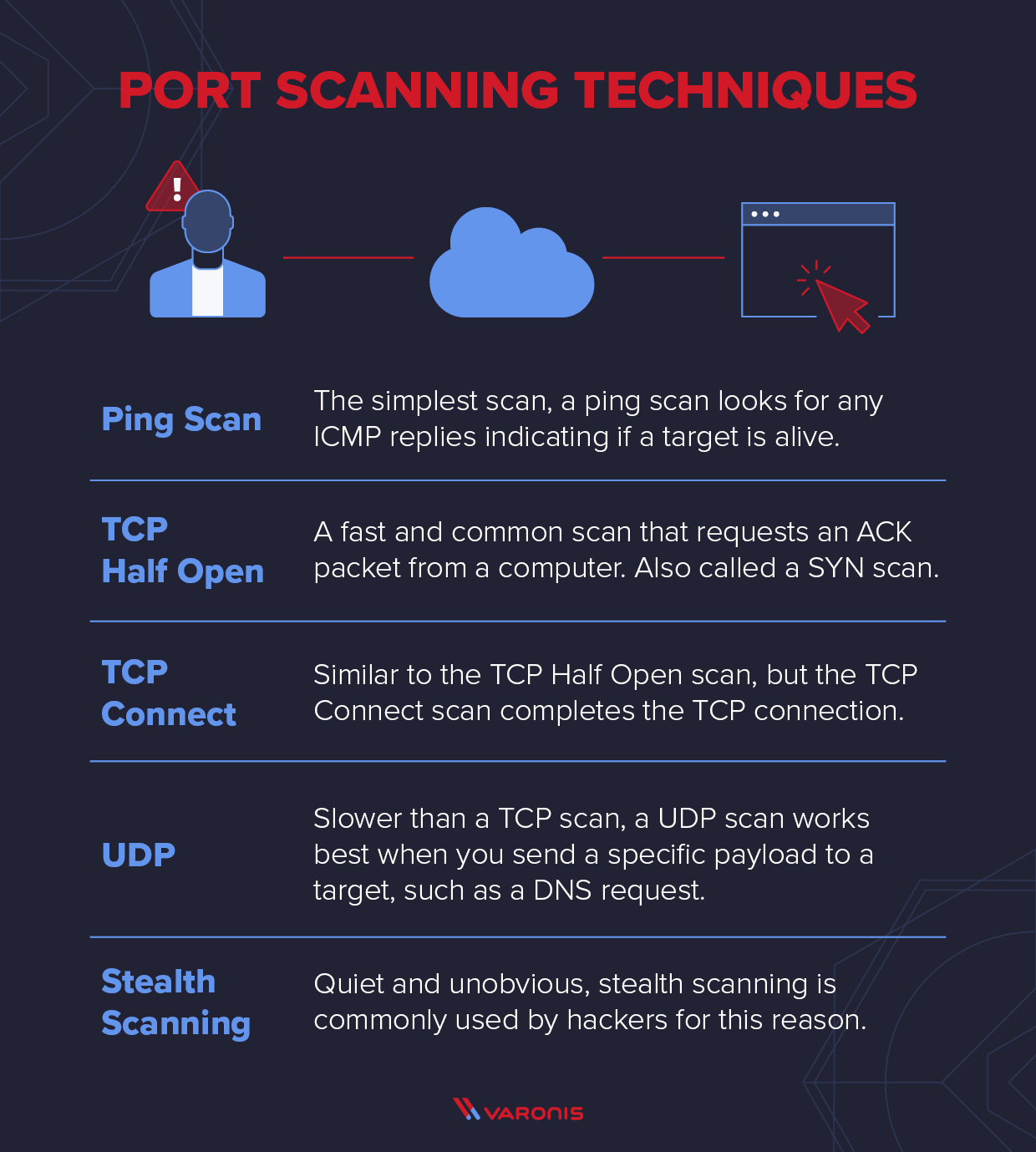 Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi09 setembro 2024
Explaining Port Scanning. A port scan is a common technique…, by Arth Awasthi09 setembro 2024 -
 Malware analysis Malicious activity09 setembro 2024
Malware analysis Malicious activity09 setembro 2024 -
Help Center09 setembro 2024
-
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 setembro 2024
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager09 setembro 2024 -
 10 Best Port Scanner Tools for Network Security - Geekflare09 setembro 2024
10 Best Port Scanner Tools for Network Security - Geekflare09 setembro 2024
você pode gostar
-
 Tatuagem na mão feminina: 64 Inspirações que nunca saem de moda09 setembro 2024
Tatuagem na mão feminina: 64 Inspirações que nunca saem de moda09 setembro 2024 -
 Mario GIFs on GIPHY - Be Animated09 setembro 2024
Mario GIFs on GIPHY - Be Animated09 setembro 2024 -
ChessBase India - YOUR CHANCE TO WIN CHESSBASE PRODUCTS09 setembro 2024
-
 Escape Game - 50 Rooms 1 - Level 22- Escape do quarto - Fase 2209 setembro 2024
Escape Game - 50 Rooms 1 - Level 22- Escape do quarto - Fase 2209 setembro 2024 -
 A Review on Demon Slayer's Main Characters (Tanjirou, Nezuko, Zenitsu & Inosuke) – PinkeuJas09 setembro 2024
A Review on Demon Slayer's Main Characters (Tanjirou, Nezuko, Zenitsu & Inosuke) – PinkeuJas09 setembro 2024 -
 Team Z ⚽ BLUE LOCK Episode 2 reaction09 setembro 2024
Team Z ⚽ BLUE LOCK Episode 2 reaction09 setembro 2024 -
 Old Modern Warfare 2 is BACK on Xbox 360! 😍 (New Servers)09 setembro 2024
Old Modern Warfare 2 is BACK on Xbox 360! 😍 (New Servers)09 setembro 2024 -
 Win 11 Pro ISO Free Download : Microsoft : Free Download, Borrow, and Streaming : Internet Archive09 setembro 2024
Win 11 Pro ISO Free Download : Microsoft : Free Download, Borrow, and Streaming : Internet Archive09 setembro 2024 -
 Crunchyroll anuncia seus animes de Primavera/Outono de 2021.09 setembro 2024
Crunchyroll anuncia seus animes de Primavera/Outono de 2021.09 setembro 2024 -
 dinossauro engraçado dos desenhos animados. jogo ponto a ponto para crianças, planilha de números. 10511196 Vetor no Vecteezy09 setembro 2024
dinossauro engraçado dos desenhos animados. jogo ponto a ponto para crianças, planilha de números. 10511196 Vetor no Vecteezy09 setembro 2024
